Generating Private Key of RSA Encryption Algorithm Using One Time Programmable On-chip Switched Capacitor Physical Unclonable Functions
-
摘要: Rivest-Shamir-Adleman(RSA)加密算法作为一种非对称加密算法,被认为是目前最安全的加密方法之一。传统RSA私钥存在存储开销大、功耗高和易受攻击等问题,针对RSA私钥面临非易失性存储器(NVM)存储依赖及物理探测攻击,该文提出一种新型RSA私钥生成架构,该方案基于SMIC 180 nm 标准CMOS工艺,利用全定制开关电容物理不可克隆函数(SC-PUF)单元产生随机密钥,采用片上1次可编程单元(OTP)将SC-PUF的输出随机密钥直接映射为满足要求的RSA私钥,完全消除NVM依赖。同时SC-PUF提供的容性敏感金属层能够有效保护OTP的编辑状态不被攻击者获取,保证了整个密钥产生电路的安全性。实验结果显示,芯片总体面积为18.77 mm2,功耗218 mW,基于SC-PUF和OTP的RSA私钥产生电路不仅能够有效产生密钥,且整个RSA算法工作正常,验证了该新型RSA私钥生成架构的可行性和安全性。Abstract:
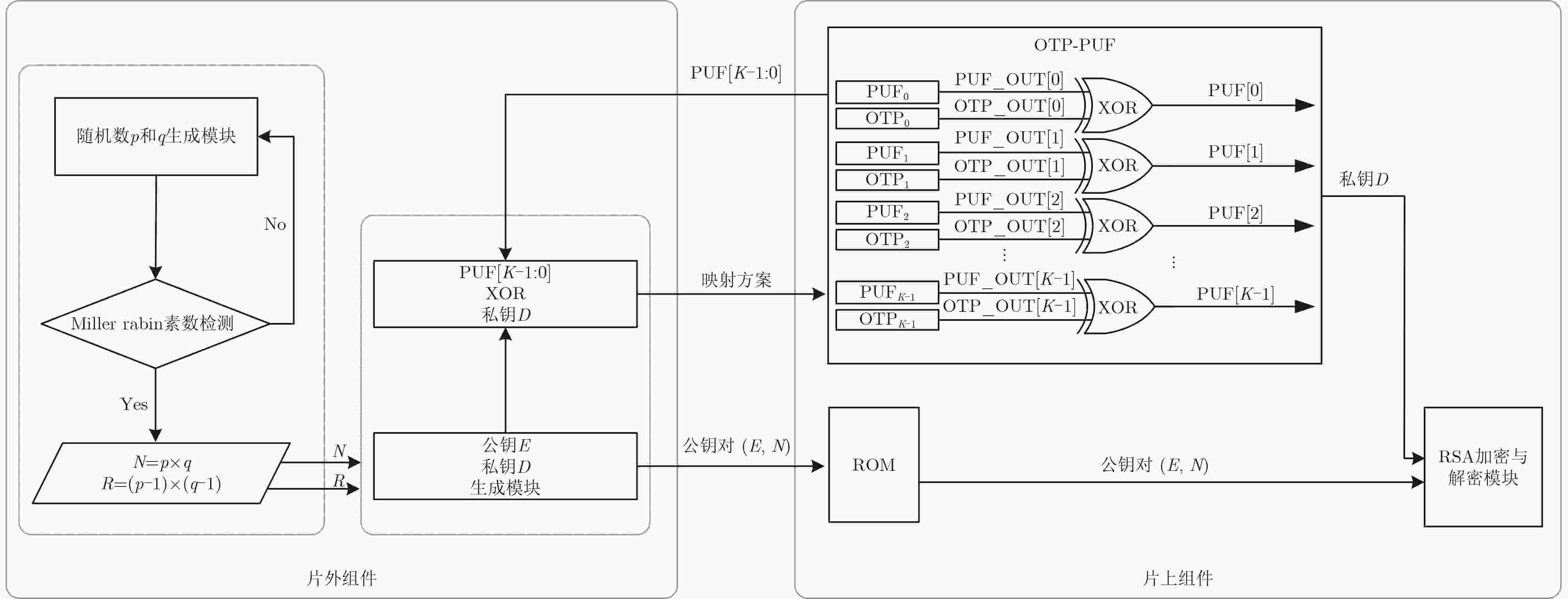
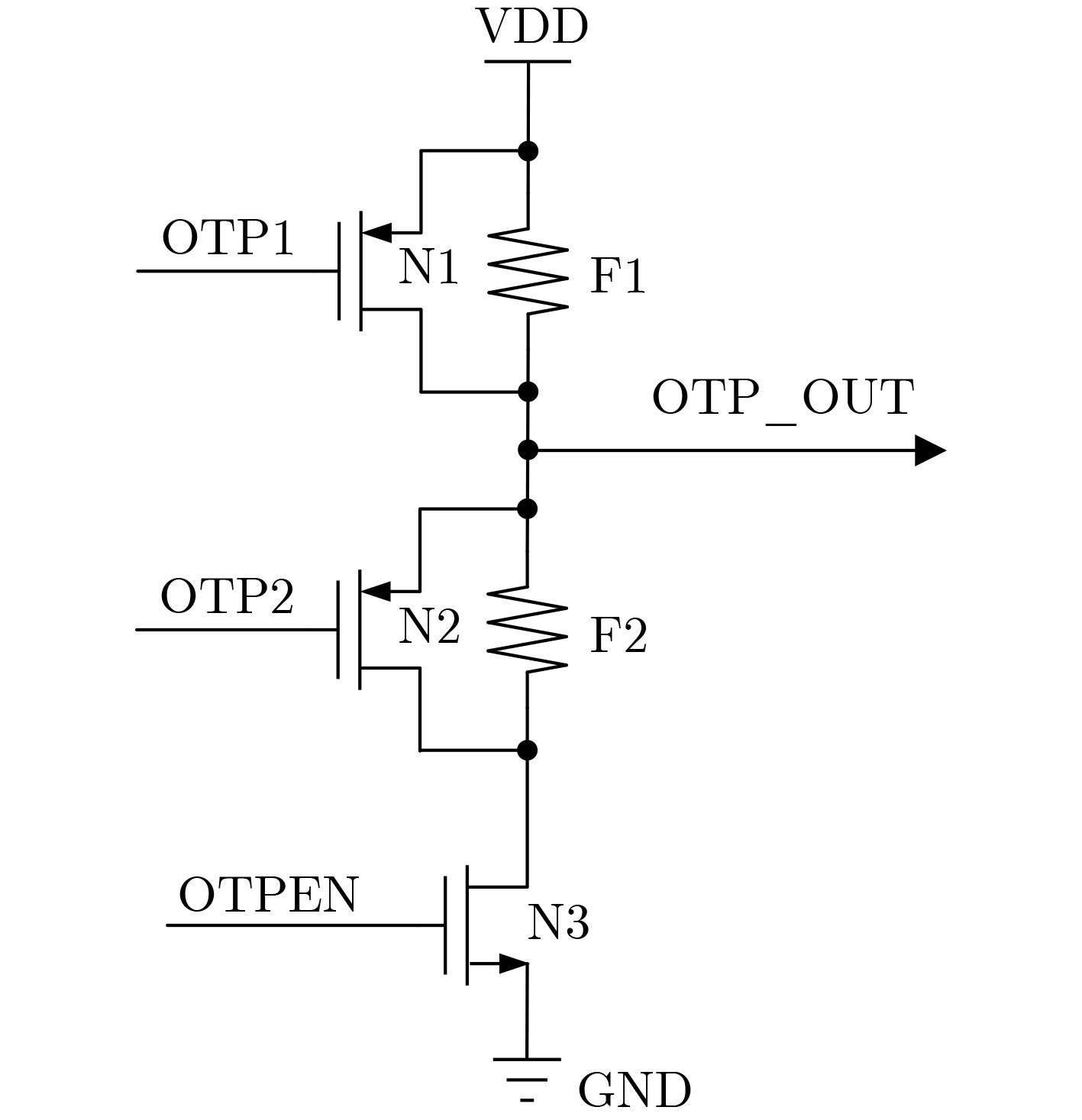
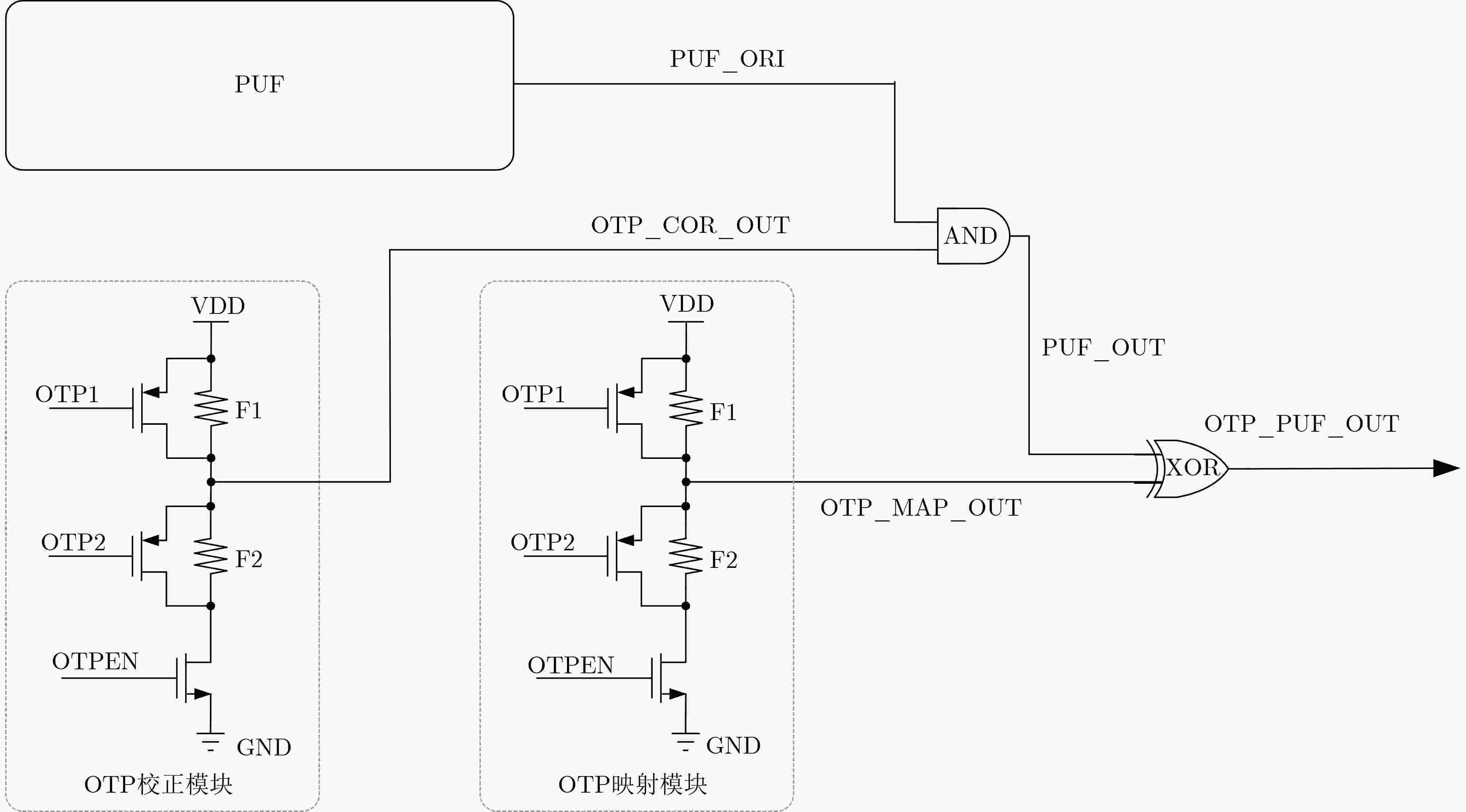
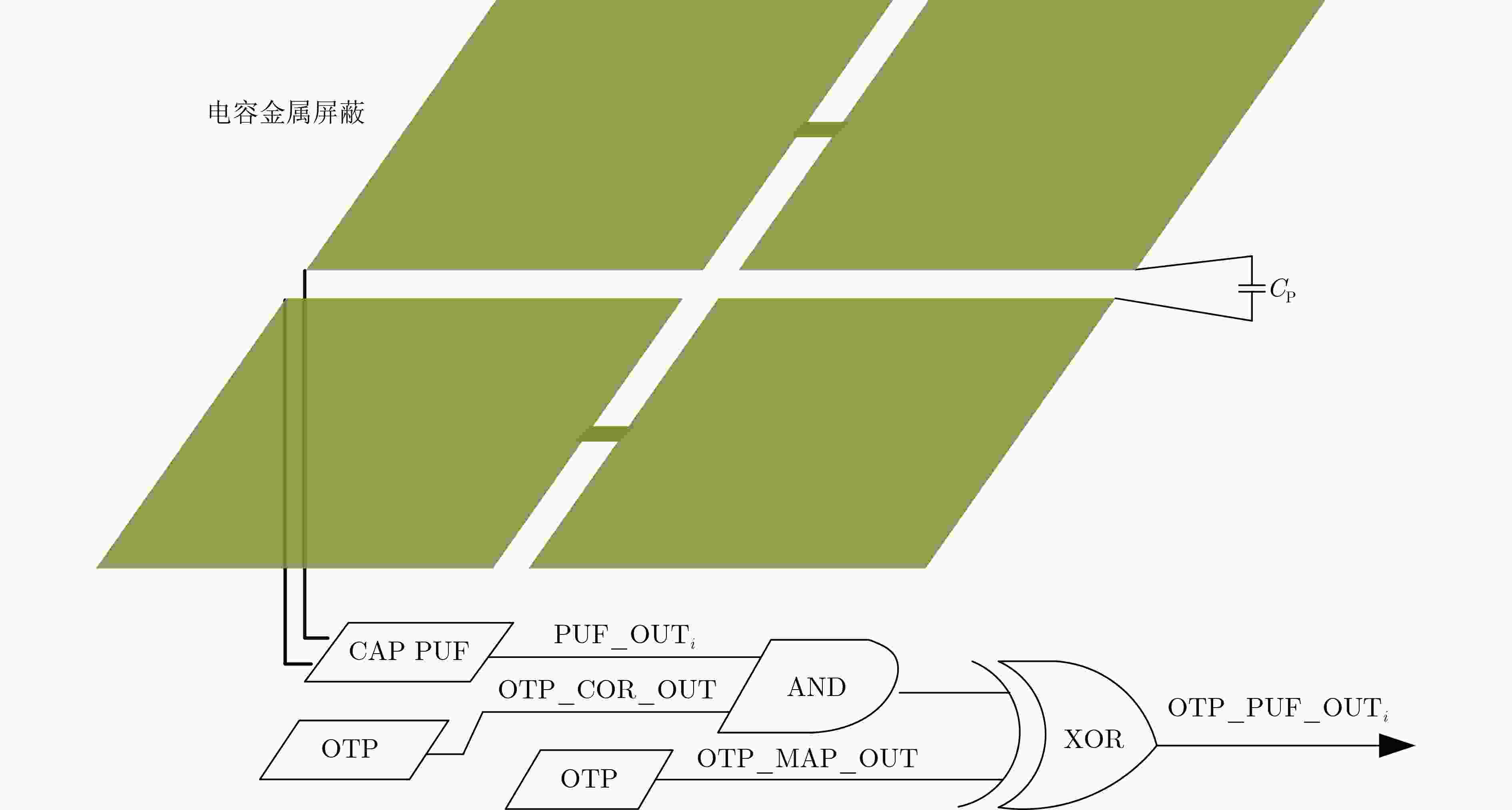
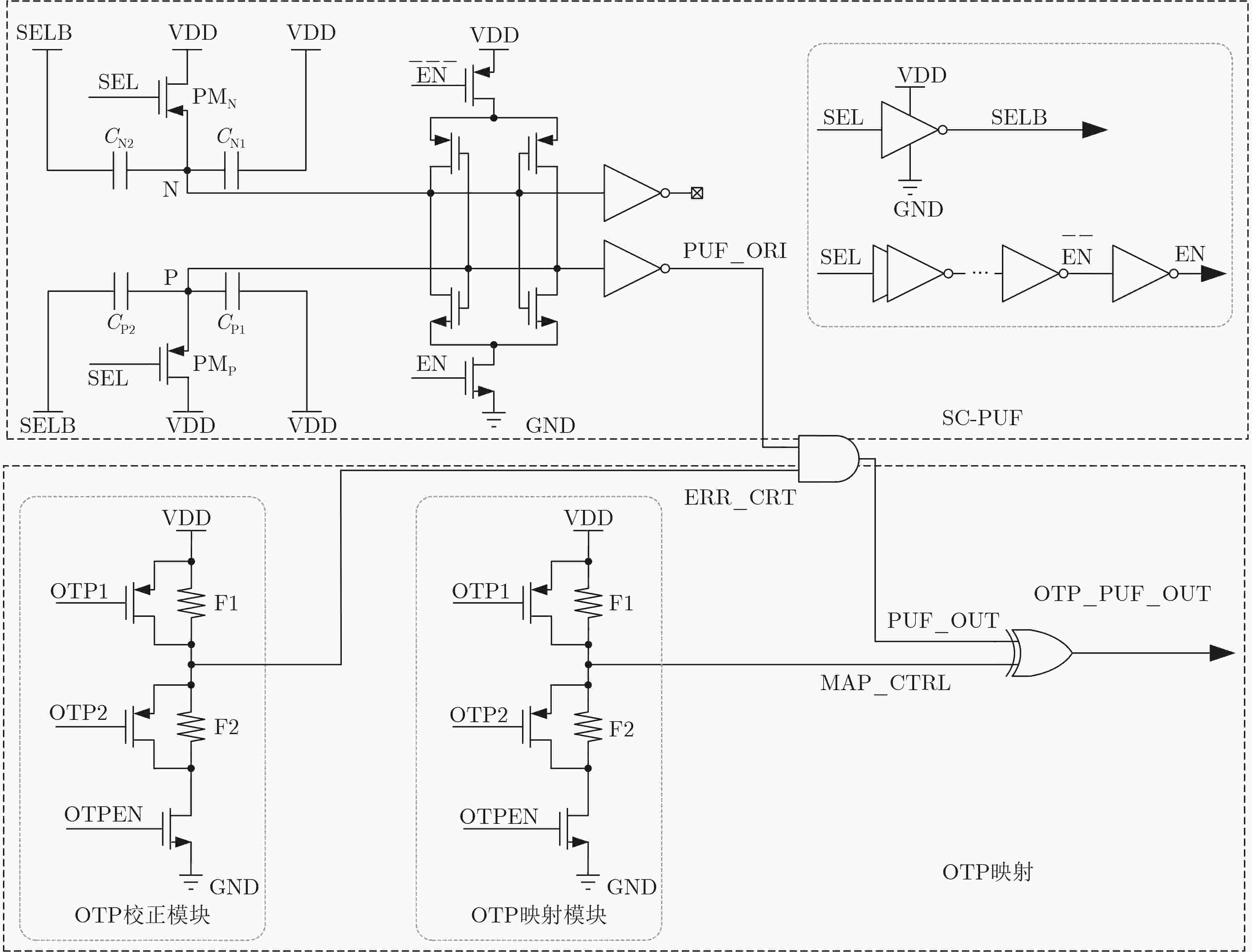
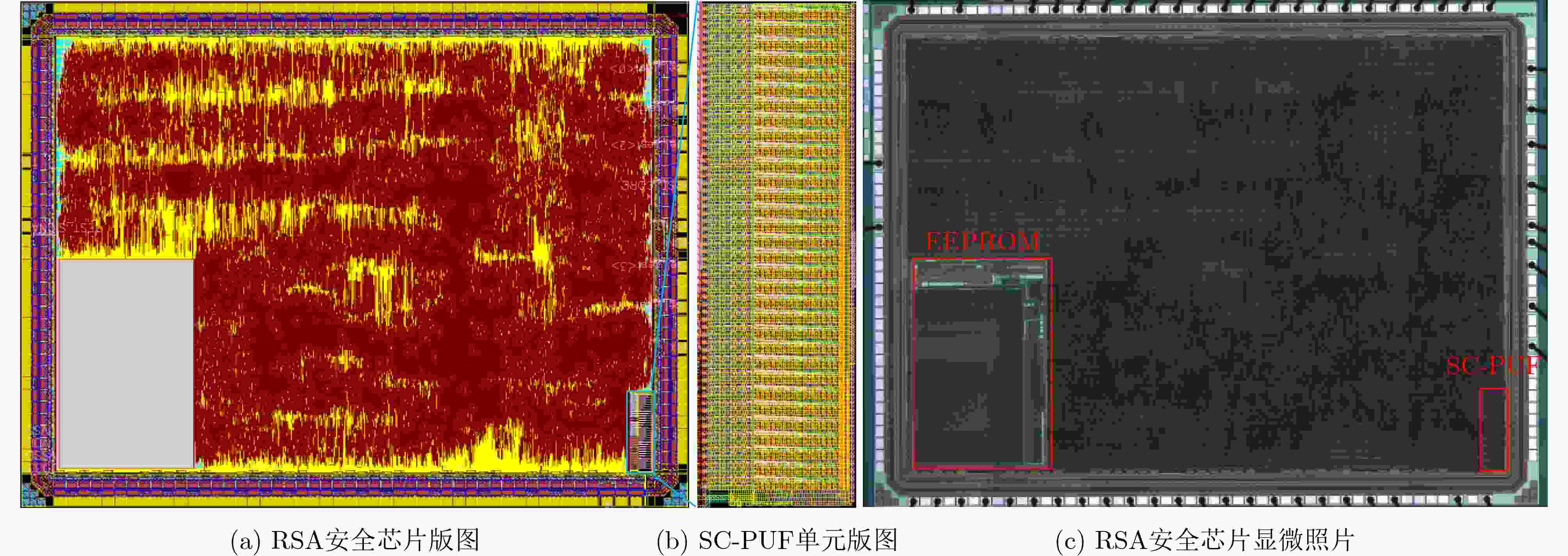
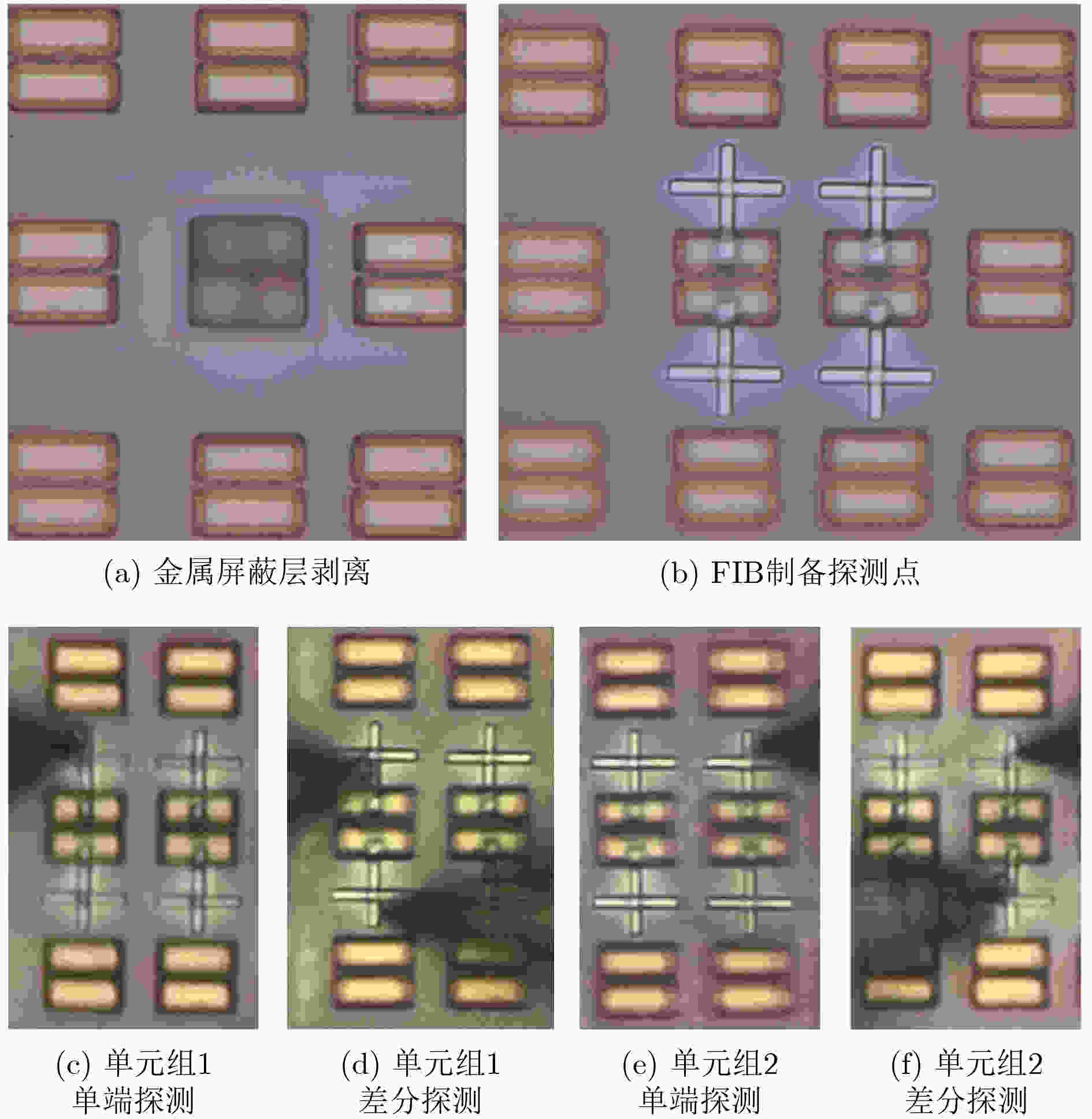
Objective RSA, an asymmetric encryption algorithm, is widely recognized as one of the most secure cryptographic methods. Conventional Rivest-Shamir-Adleman(RSA) private keys face challenges of high storage overhead, power consumption, and vulnerability to attacks. To address the dependency on Non-Volatile Memory (NVM) and the risk of physical probing, a novel RSA private key generation architecture is proposed. The design utilizes fully customized Switched Capacitor Physical Unclonable Functions(SC-PUF) cells for random key generation. By mapping the initial output codes of the weak Physical Unclonable Functions(PUF) to the final private key using One-Time Programmable (OTP) memory, the circuit eliminates the need for independent NVM such as flash or EEPROM. This reduces power and area consumption as well as factory testing costs. An integrated capacitive metal shielding layer in the SC-PUF prevents OTP state compromise, thereby ensuring secure key generation. Methods The proposed OTP mapping-based scheme is implemented and validated in a security ASIC. A low-cost capacitive SC-PUF circuit is employed to generate stable initial PUF keys through capacitance ratio mismatch sampling, with comprehensive shielding applied to protect the entire PUF and OTP circuitry from invasive attacks. To further mitigate such attacks, Metal-Insulator-Metal (MIM) capacitors constructed from two high-layer metals are used to realize the sense capacitor of the SC-PUF. Both the PUF and OTP circuits are encapsulated within a capacitive-sensitive protective layer. An on-chip CMOS-compatible eFuse-based OTP serves as the mapping circuit, and the OTP, PUF extraction circuit, and mapping circuit are placed beneath the capacitive metal coating provided by the PUF. This architecture enables secure, low-cost, and power-efficient private key generation. Results and Discussions The defensive efficacy of SC-PUF and metal shielding against invasive attacks is evaluated by removing the corresponding top metal layer using Focused Ion Beam (FIB) techniques. Although the state of the poly eFuse is directly exposed, complete removal of the top metal layer alters the output key of the SC-PUF ( Fig. 7a ,b ). In a potential attack scenario, all SC-PUF keys may be probed first, followed by metal layer removal to reveal the eFuse state, with the aim of reconstructing the original PUF output codes and mapping control signals. To assess the protective capability of the proposed architecture against such attacks, probing experiments are conducted on the metal layer to determine whether SC-PUF keys can be externally extracted. A total of eight key units are probed (Fig. 7c –f ). The results show that single-ended probing of the top metal layer leads to a rapid increase in parasitic capacitance to ground, which consistently forces the corresponding output code to 0 (Fig. 7c ,e ). In contrast, differential probing introduces parasitic capacitance mismatch larger than the original MIM capacitor mismatch, resulting in deviation of the probed output codes from the original values (Fig. 7d ,f ). Among the eight SC-PUF units tested, five exhibit probe results that differ from the original output codes. These observations indicate that probing the metal layer changes the keys due to parasitic capacitance variations, and the extracted information does not represent the true SC-PUF outputs. Therefore, even if the eFuse state is exposed, the SC-PUF keys cannot be reconstructed and the RSA private key cannot be derived. Additionally, existing implementations generally rely on on-chip NVM to store private keys, making them susceptible to data bus-based probing attacks (Table 1 ). In contrast, the proposed scheme employs OTP to map the initial weak PUF output codes to the final private key, thereby eliminating the need for independent NVM (Table 1 ). Although the RSA-2048 algorithm increases logic complexity, leading to a higher gate count and a slight reduction in speed, the proposed OTP mapping-based private key generation circuit achieves a throughput of 187.09 kbps at a power consumption of 218 mW, corresponding to an energy efficiency of 0.858 kbps/mW (Table 1 ).Conclusions To address the dependency on NVM storage and the vulnerability of RSA private keys to physical probing, a novel OTP mapping-based private key generation scheme is proposed. The scheme is programmed at the wafer testing stage, directly mapping the raw PUF output to the target RSA private key, thereby reducing circuit overhead and enabling real-time key generation. This approach effectively mitigates the risk of key interception. Experimental results confirm two key advantages: (1) by mapping the initial output codes of the weak PUF to the final private key through OTP, the scheme eliminates the need for NVM, lowers power and area consumption, and reduces factory test cost. The prototype, fabricated in SMIC 180 nm CMOS technology, occupies 18.77 mm2 and consumes 218 mW; (2) the integrated SC-PUF and metal shielding layer provide effective protection against invasive attacks. This work represents the first application of PUF to RSA private key generation. Furthermore, the proposed scheme can be extended to other asymmetric encryption algorithms requiring private keys, including SM4 and ECC. -
[1] BURKHARDT J, DAMGÅRD I, FREDERIKSEN T K, et al. Improved distributed RSA key generation using the miller-Rabin test[C]. The 2023 ACM SIGSAC Conference on Computer and Communications Security, Copenhagen, Denmark, 2023: 2501–2515. doi: 10.1145/3576915.3623163. [2] TYAGI N, FISCH B, ZITEK A, et al. VeRSA: Verifiable registries with efficient client audits from RSA authenticated dictionaries[C]. The 2022 ACM SIGSAC Conference on Computer and Communications Security, Los Angeles, USA, 2022: 2793–2807. doi: 10.1145/3548606.3560605. [3] KEMMOE V Y and LYSYANSKAYA A. RSA-based dynamic accumulator without hashing into primes[C]. The 2024 on ACM SIGSAC Conference on Computer and Communications Security, Salt Lake City, USA, 2024: 4271–4285. doi: 10.1145/3658644.3690199. [4] DIMITROV V, VIGNERI L, and ATTIAS V. Fast generation of RSA keys using smooth integers[J]. IEEE Transactions on Computers, 2022, 71(7): 1575–1585. doi: 10.1109/TC.2021.3095669. [5] REDDY S S, SINHA S, and ZHANG Wei. Design and analysis of RSA and paillier homomorphic cryptosystems using PSO-based evolutionary computation[J]. IEEE Transactions on Computers, 2023, 72(7): 1886–1900. doi: 10.1109/TC.2023.3234213. [6] SALA R D, BELLIZIA D and SCOTTI G. Unveiling the true power of the latched ring oscillator for a unified PUF and TRNG architecture[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2024, 32(12): 2403–2407. doi: 10.1109/TVLSI.2024.3448503. [7] REN Qirui, HUO Qiang, CHEN Zhisheng, et al. A security-enhanced, charge-pump-free, ISO14443-A-/ISO10373–6-compliant RFID tag with 16.2-μW embedded RRAM and reconfigurable strong PUF[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2023, 31(2): 243–252. doi: 10.1109/TVLSI.2022.3222522. [8] AGHAPOUR S, AHMADI K, ANASTASOVA M, et al. PUF-Kyber: Design of a PUF-Based Kyber architecture benchmarked on diverse ARM processors[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2024, 43(12): 4453–4462. doi: 10.1109/TCAD.2024.3399669. [9] LAO Yingjie and PARHI K K. Statistical analysis of MUX-based physical unclonable functions[J]. IEEE Transactions on Computer-Aided Design of Integrated Circuits and Systems, 2014, 33(5): 649–662. doi: 10.1109/TCAD.2013.2296525. [10] SAHOO D P, MUKHOPADHYAY D, CHAKRABORTY R S, et al. A multiplexer-based arbiter PUF composition with enhanced reliability and security[J]. IEEE Transactions on Computers, 2018, 67(3): 403–417. doi: 10.1109/TC.2017.2749226. [11] USMANI M A, KESHAVARZ S, MATTHEWS E, et al. Efficient PUF-based key generation in FPGAs using per-device configuration[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2019, 27(2): 364–375. doi: 10.1109/TVLSI.2018.2877438. [12] WAN Meilin, HE Zhangqing, HAN Shuang, et al. An invasive-attack-resistant PUF based on switched-capacitor circuit[J]. IEEE Transactions on Circuits and Systems I: Regular Papers, 2015, 62(8): 2024–2034. doi: 10.1109/TCSI.2015.2440739. [13] ZHANG Yin, HE Zhangqing, WAN Meilin, et al. A SC PUF standard cell used for key generation and anti-invasive-attack protection[J]. IEEE Transactions on Information Forensics and Security, 2021, 16: 3958–3973. doi: 10.1109/TIFS.2021.3089854. [14] SHIEH M D, CHEN Junhong, WU H H, et al. A new modular exponentiation architecture for efficient design of RSA cryptosystem[J]. IEEE Transactions on Very Large Scale Integration (VLSI) Systems, 2008, 16(9): 1151–1161. doi: 10.1109/TVLSI.2008.2000524. [15] LIU Qiang, MA Fangzhen, TONG Dong, et al. A regular parallel RSA processor[C]. The 2004 47th Midwest Symposium on Circuits and Systems, Hiroshima, Japan, 2004: iii–467. doi: 10.1109/MWSCAS.2004.1354396. [16] KWON T W, YOU C S, HEO W S, et al. Two implementation methods of a 1024-bit RSA cryptoprocessor based on modified Montgomery algorithm[C]. 2001 IEEE International Symposium on Circuits and Systems, Sydney, Australia, 2001: 650–653. doi: 10.1109/ISCAS.2001.922321. -





 下载:
下载:


 下载:
下载:
