A Two-Stage Framework for CAN Bus Attack Detection by Fusing Temporal and Deep Features
-
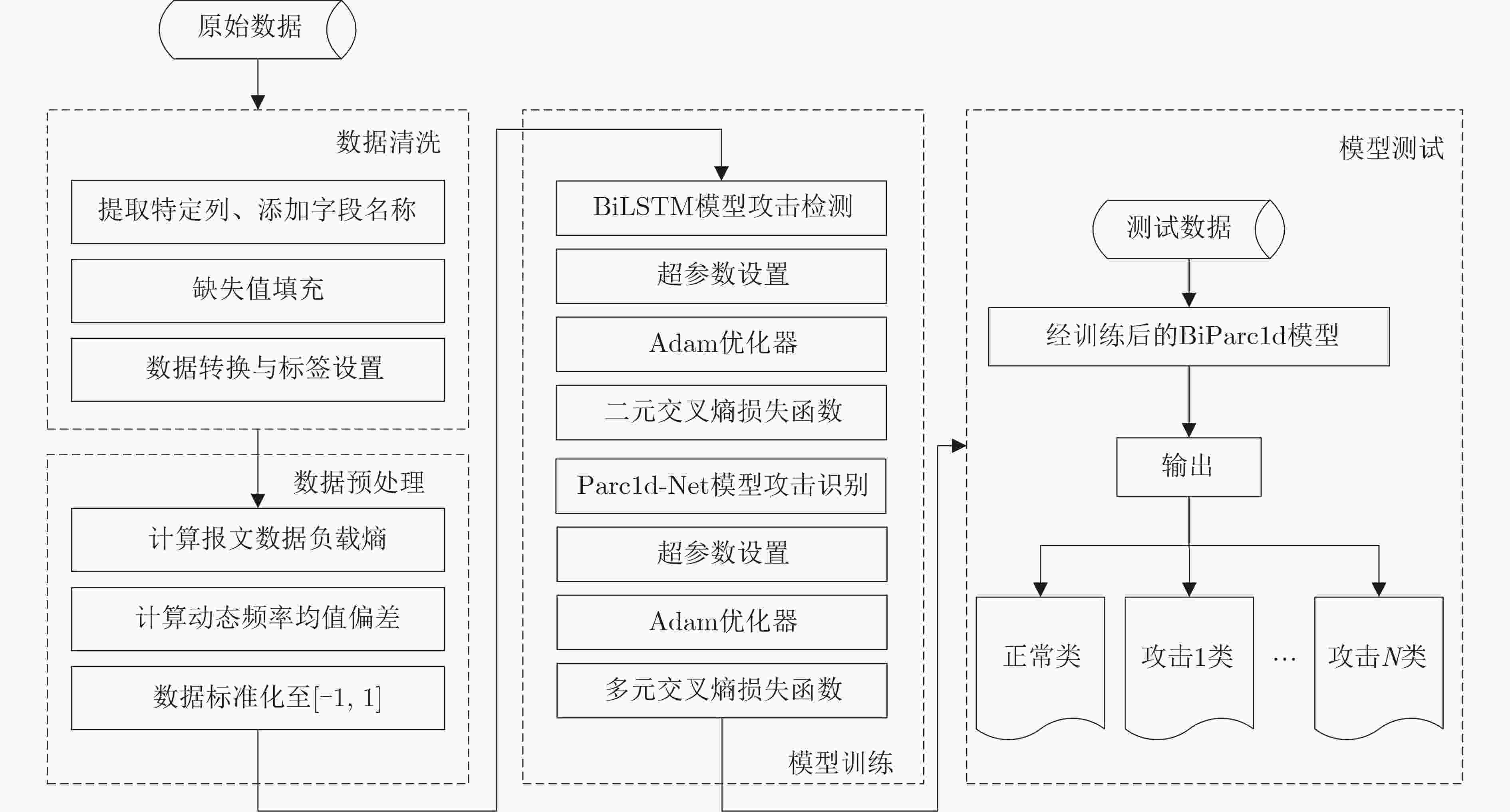
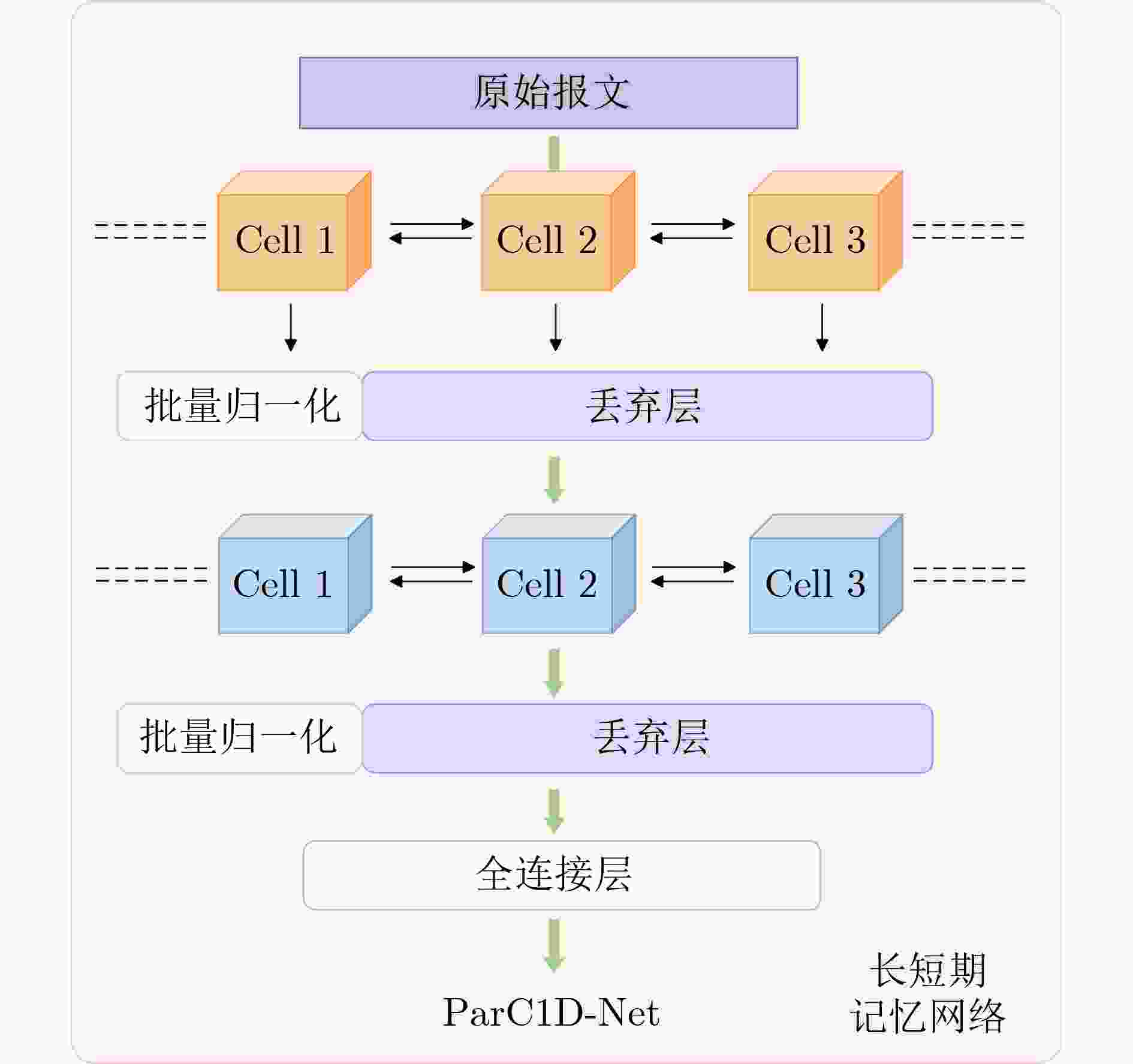
摘要: 控制器局域网(CAN)因安全机制缺失易遭受网络攻击,现有入侵检测系统在多类攻击识别和车载部署上仍存在挑战。该文提出一种融合时序与深度特征的二阶段CAN总线攻击识别方法,通过“先检测、后分类”的策略,将复杂任务分解,实现效率与精度统一。第1阶段设计了数据负载熵(PDE)与ID频率均值偏差(IFMD)特征,从内容与行为2个维度量化报文异常,并利用双向长短期记忆网络(BiLSTM)捕捉时序依赖,实现高效异常检测;第2阶段针对异常样本,引入一维轻量化ParC1D-Net,通过深度特征精细分析实现多类攻击分类。公开数据集实验表明,该方法在Car-Hacking数据集上准确率和F1分数均达99.99%,优于多种先进方法;消融实验验证PDE与IFMD特征在提升异常检测敏感性和鲁棒性方面的关键作用。此外,方法在GPU和模拟嵌入式CPU环境下测试,模型大小仅0.39 MB,实时检测时延分别为0.62 ms和0.93 ms,具备良好部署与实时处理能力。
-
关键词:
- 入侵检测 /
- 控制器局域网络(CAN) /
- 二阶段框架 /
- 特征提取
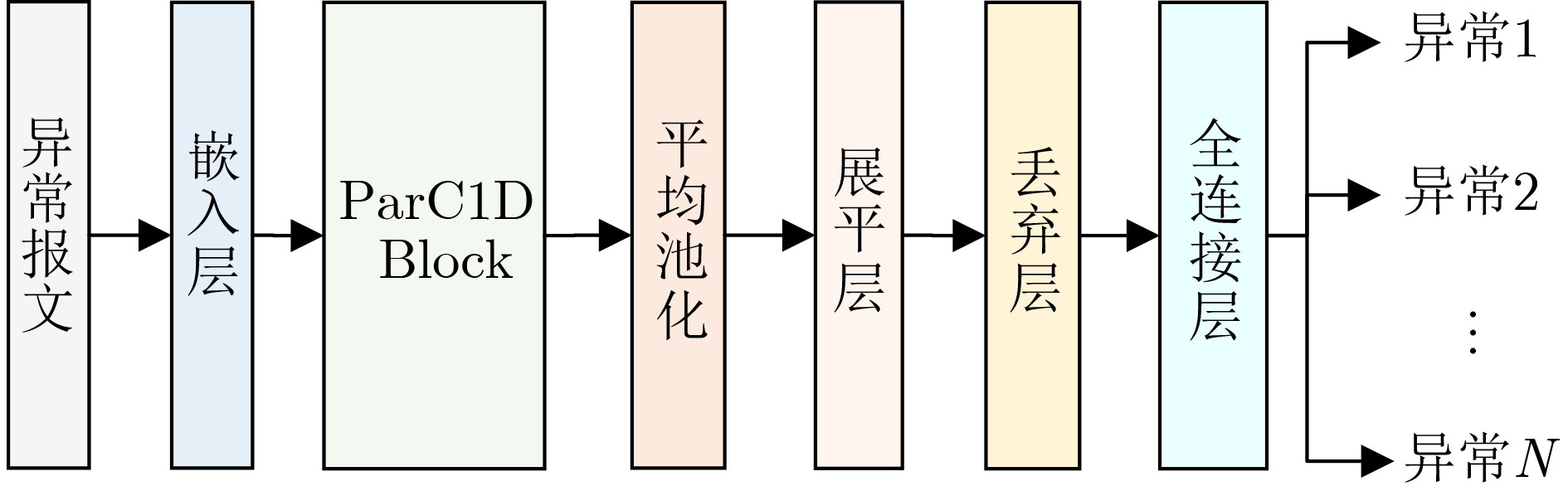
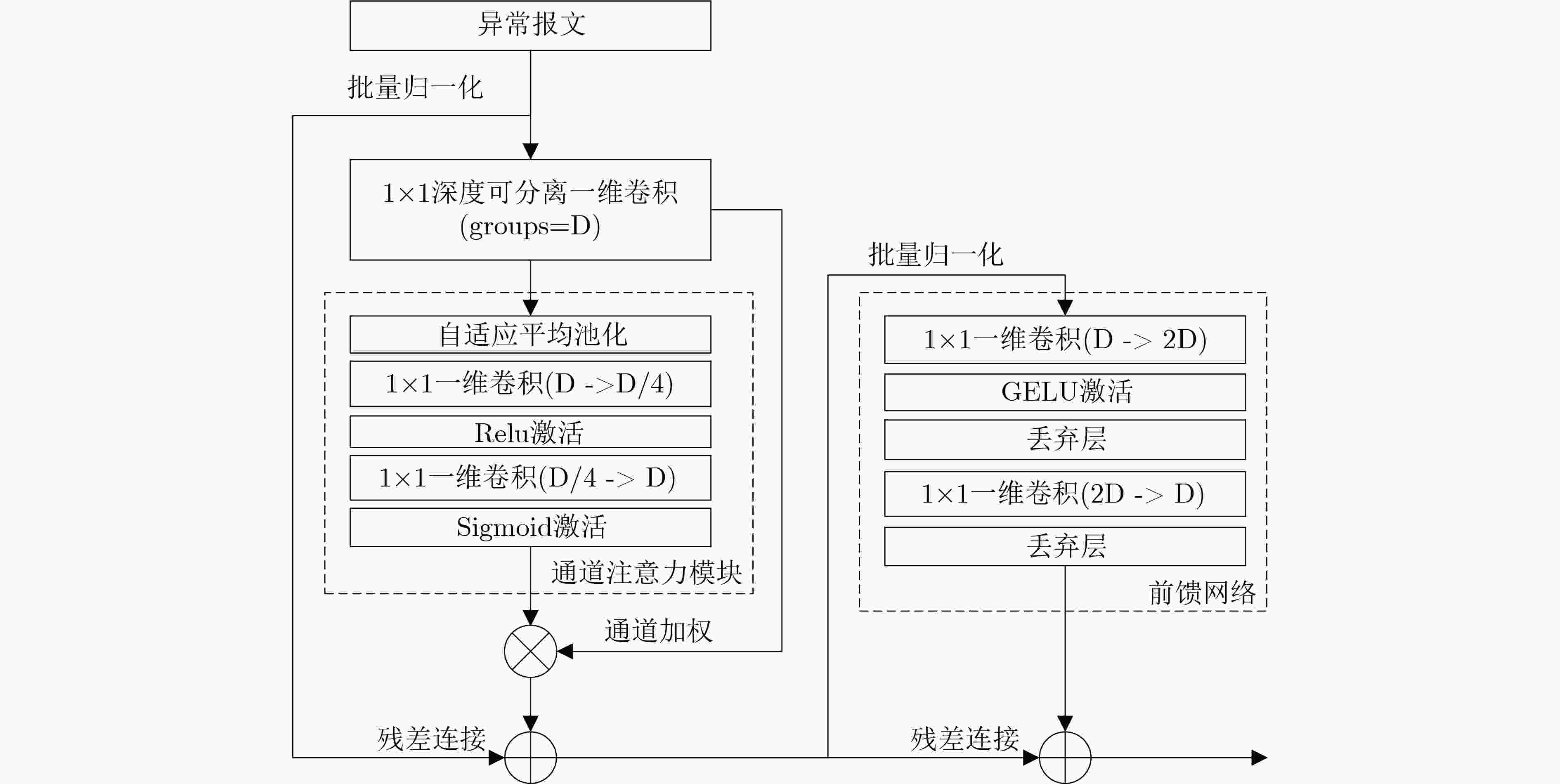
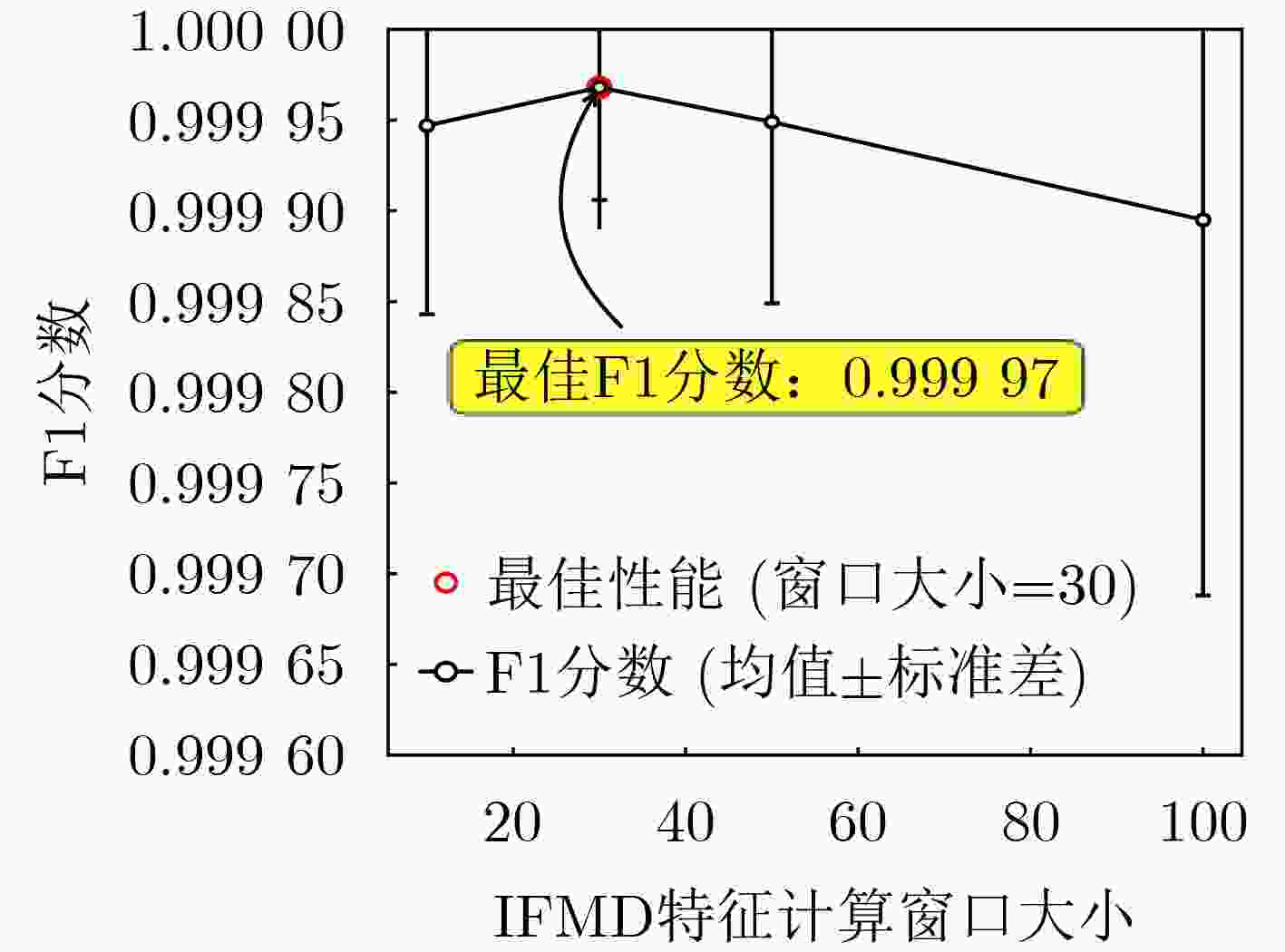
Abstract:Objective The Controller Area Network (CAN), the de facto standard for in-vehicle communication, is inherently vulnerable to cyberattacks. Existing Intrusion Detection Systems (IDSs) face a fundamental trade-off: achieving fine-grained classification of diverse attack types often requires computationally intensive models that exceed the resource limitations of on-board Electronic Control Units (ECUs). To address this problem, this study proposes a two-stage attack detection framework for the CAN bus that fuses temporal and deep features. The framework is designed to achieve both high classification accuracy and computational efficiency, thereby reconciling the tension between detection performance and practical deployability. Methods The proposed framework adopts a “detect-then-classify” strategy and incorporates two key innovations. (1) Stage 1: Temporal Feature-Aware Anomaly Detection. Two custom features are designed to quantify anomalies: Payload Data Entropy (PDE), which measures content randomness, and ID Frequency Mean Deviation (IFMD), which captures behavioral deviations. These features are processed by a Bidirectional Long Short-Term Memory (BiLSTM) network that exploits contextual temporal information to achieve high-recall anomaly detection. (2) Stage 2: Deep Feature-Based Fine-Grained Classification. Triggered only for samples flagged as anomalous, this stage employs a lightweight one-dimensional ParC1D-Net. The core ParC1D Block ( Fig. 4 ) integrates depthwise separable one-dimensional convolution, Squeeze-and-Excitation (SE) attention, and a Feed-Forward Network (FFN), enabling efficient feature extraction with minimal parameters. Stage 1 is optimized using BCEWithLogitsLoss, whereas Stage 2 is trained with Cross-Entropy Loss.Results and Discussions The efficacy of the proposed framework is evaluated on public datasets. (1) State-of-the-art performance. On the Car-Hacking dataset ( Table 5 ), an accuracy and F1-score of 99.99% are achieved, exceeding advanced baselines. On the more challenging Challenge dataset (Table 6 ), superior accuracy (99.90%) and a competitive F1-score (99.70% are also obtained. (2) Feature contribution analysis. Ablation studies (Tables 7 and8 ) confirm the critical role of the proposed features. Removal of the IFMD feature results in the largest performance reduction, highlighting the importance of behavioral modeling. A synergistic effect is observed when PDE and IFMD are applied together. (3) Spatiotemporal efficiency. The complete model remains lightweight at only 0.39 MB. Latency tests (Table 9 ) demonstrate real-time capability, with average detection times of 0.62 ms on a GPU and 0.93 ms on a simulated CPU (batch size = 1). A system-level analysis (Section 3.5.4) further shows that the two-stage framework is approximately 1.65 times more efficient than a single-stage model in a realistic sparse-attack scenario.Conclusions This study establishes the two-stage framework as an effective and practical solution for CAN bus intrusion detection. By decoupling detection from classification, the framework resolves the trade-off between accuracy and on-board deployability. Its strong performance, combined with a minimal computational footprint, indicates its potential for securing real-world vehicular systems. Future research could extend the framework and explore hardware-specific optimizations. -
表 1 二阶段模型关键参数设置
模型参数 第1阶段: BiLSTM模型 第2阶段:ParC1D-Net模型 批量大小设置 1024 1024 滑动窗口大小 30 不适用 (N/A) 损失函数 BCEWithLogitsLoss CrossEntropyLoss 优化器 Adam AdamW 优化器学习率 0.001 0.001 Epoch设置 5 5 Dropout率 0.5 0.5 表 2 Car-Hacking数据分布情况
攻击类型 总报文数量 正常报文数量 攻击报文数量 DoS 3 665 771 3 078 250 587 521 Fuzzy 3 838 860 3 347 013 491 847 Gear 4 443 142 3 845 890 597 252 RPM 4 621 702 3 966 805 654 897 表 3 Challenge数据分布情况
报文类型 总报文数量 DoS 587 521 Fuzzy 196 979 Gear 597 252 RPM 654 897 Attack free 11 742 542 表 4 Car-Hacking数据集上不同算法间多分类性能比较(%)
表 5 Challenge数据集上不同算法间多分类性能比较(%)
表 6 Car-Hacking数据集消融实验结果表(%)
模型 准确率 精确率 召回率 F1 本文模型 99.9 988 ± 0.0 000 99.9 986 ± 0.0 001 99.9 965 ± 0.0 002 99.9 976 ± 0.0 001 w/o PDE 99.9 977 ± 0.0 002 99.9 974 ± 0.0 001 99.9 936 ± 0.0 007 99.9 955 ± 0.0 004 w/o IFMD 99.9 239 ± 0.0 014 99.7 876 ± 0.0 058 99.9 109 ± 0.0 103 99.8 491 ± 0.0 028 w/o PDE&IFMD 99.9 092 ± 0.0 096 99.7 505 ± 0.0 273 99.8 899 ± 0.0 129 99.8 200 ± 0.0 190 表 7 Challenge数据集消融实验结果表(%)
模型 准确率 精确率 召回率 F1 本文模型 99.9 037 ± 0.0 029 99.8 622±0.0 068 99.5 414±0.0 131 99.7 012±0.0 089 w/o PDE 99.8 743 ± 0.0 060 99.8 201 ± 0.0 077 99.4 017 ± 0.0 323 99.6 098 ± 0.0 185 w/o IFMD 99.8 578 ± 0.0 105 99.8 168 ± 0.0 130 99.3 026 ± 0.0 619 99.5 580 ± 0.0 329 w/o PDE&IFMD 99.8 279 ± 0.0 110 99.7 336 ± 0.0 507 99.2 003 ± 0.0 540 99.4 651 ± 0.0 342 表 8 不同算法间时空性能比较
表 9 不同算法间时空性能比较
模型 模型大小 (MB) 推理时延 (ms/样本, bs=1) 单阶段-BiLSTM (多分类) 0.3 128 0.9 300 二阶段-S1-BiLSTM 0.3 118 0.5 628 二阶段-S2-ParC1D-Net 0.0 777 0.6 635 -
[1] 钱志鸿, 田春生, 郭银景, 等. 智能网联交通系统的关键技术与发展[J]. 电子与信息学报, 2020, 42(1): 2–19. doi: 10.11999/JEIT190787.QIAN Zhihong, TIAN Chunsheng, GUO Yinjing, et al. The key technology and development of intelligent and connected transportation system[J]. Journal of Electronics & Information Technology, 2020, 42(1): 2–19. doi: 10.11999/JEIT190787. [2] LAMPE B and MENG W Z. Intrusion detection in the automotive domain: A comprehensive review[J]. IEEE Communications Surveys & Tutorials, 2023, 25(4): 2356–2426. doi: 10.1109/COMST.2023.3309864. [3] WANG L X, ZHAO Q C, LEE W B, et al. Deploying intrusion detection on in-vehicle networks: Challenges and opportunities[J]. IEEE Network, 2025, 39(1): 306–312. doi: 10.1109/MNET.2024.3486220. [4] WU W F, LI R F, XIE G Q, et al. A survey of intrusion detection for in-vehicle networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2020, 21(3): 919–933. doi: 10.1109/TITS.2019.2908074. [5] KHEZRI E, HASSANZADEH H, YAHYA R O, et al. Security challenges in internet of vehicles (IoV) for ITS: A survey[J]. Tsinghua Science and Technology, 2025, 30(4): 1700–1723. doi: 10.26599/TST.2024.9010083. [6] LAMPE B and MENG W Z. A survey of deep learning-based intrusion detection in automotive applications[J]. Expert Systems with Applications, 2023, 221: 119771. doi: 10.1016/j.eswa.2023.119771. [7] ZHANG H K, HU W Z, and WANG X Y. ParC-Net: Position aware circular convolution with merits from ConvNets and transformer[C]. Proceedings of the 17th European Conference on Computer Vision, Tel Aviv, Israel, 2022: 613–630. doi: 10.1007/978-3-031-19809-0_35. [8] SEO E, SONG H M, and KIM H K. GIDS: GAN based intrusion detection system for in-vehicle network[C]. Proceedings of 2018 16th Annual Conference on Privacy, Security and Trust (PST), Belfast, Ireland, 2018: 1–6. doi: 10.1109/PST.2018.8514157. [9] KANG H, KWAK B I, LEE Y H, et al. Car hacking and defense competition on in-vehicle network[C]. Proceedings of Workshop on Automotive and Autonomous Vehicle Security (AutoSec) 2021, San Diego, CA, USA, 2021, 2021: 25. doi: 10.14722/autosec.2021.23035. [10] KHAN I A, MOUSTAFA N, PI D C, et al. An enhanced multi-stage deep learning framework for detecting malicious activities from autonomous vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2022, 23(12): 25469–25478. doi: 10.1109/TITS.2021.3105834. [11] ALMUTLAQ S, DERHAB A, HASSAN M M, et al. Two-stage intrusion detection system in intelligent transportation systems using rule extraction methods from deep neural networks[J]. IEEE Transactions on Intelligent Transportation Systems, 2023, 24(12): 15687–15701. doi: 10.1109/TITS.2022.3202869. [12] CHOUGULE A, KULKARNI I, ALLADI T, et al. HybridSecNet: In-vehicle security on controller area networks through a hybrid two-step LSTM-CNN model[J]. IEEE Transactions on Vehicular Technology, 2024, 73(10): 14580–14591. doi: 10.1109/TVT.2024.3413849. [13] ALJABRI W, HAMID M A, and MOSLI R. Enhancing real-time intrusion detection system for in-vehicle networks by employing novel feature engineering techniques and lightweight modeling[J]. Ad Hoc Networks, 2025, 169: 103737. doi: 10.1016/j.adhoc.2024.103737. [14] 李思涌, 吴书汉, 孙伟. 基于注意力机制的CNN-LSTM网络车内CAN总线入侵检测技术[J]. 信息安全研究, 2023, 9(10): 961–967. doi: 10.12379/j.issn.2096-1057.2023.10.05.LI S Y, WU S H, and SUN W. A CNN-LSTM method based on attention mechanism for in-vehicle CAN bus intrusion detection[J]. Journal of Information Security Research, 2023, 9(10): 961–967. doi: 10.12379/j.issn.2096-1057.2023.10.05. [15] JEONG Y, KIM H, LEE S, et al. In-vehicle network intrusion detection system using CAN frame-aware features[J]. IEEE Transactions on Intelligent Transportation Systems, 2024, 25(5): 3843–3853. doi: 10.1109/TITS.2023.3323622. [16] 陈彦彬, 刘桂雄. 双线性自注意力机制CAN总线入侵检测方法研究[J]. 电子测量技术, 2025, 48(2): 122–130. doi: 10.19651/j.cnki.emt.2417438.CHEN Y B and LIU G X. Study on bilinear self-attention mechanism for CAN bus intrusion detection method[J]. Electronic Measurement Technology, 2025, 48(2): 122–130. doi: 10.19651/j.cnki.emt.2417438. [17] CHENG P Z, XU K, LI S M, et al. TCAN-IDS: Intrusion detection system for internet of vehicle using temporal convolutional attention network[J]. Symmetry, 2022, 14(2): 310. doi: 10.3390/sym14020310. -





 下载:
下载:


 下载:
下载:
