An Implicit Certificate-Based Lightweight Authentication Scheme for Power Industrial Internet of Things
-
摘要: 随着电力工业互联网的快速发展,电力系统与互联网的深度融合在推动产业智能化升级的同时,也带来了严峻的安全挑战。资源受限的终端使电力设备易遭受恶意攻击,亟须高效安全的身份认证机制以保障系统内的数据安全传输。然而,现有认证方案计算开销较大,且在应对常见攻击时仍存在安全隐患,难以满足电力工业互联网的实际需求。针对这一问题,该文设计了一种安全轻量的身份认证方案。在设备注册阶段引入隐式证书技术,将公钥认证信息嵌入签名中,从而无须显式传输完整的证书信息。相比传统证书,隐式证书更短且验证效率更高,有效降低了传输与验证开销。在此基础上,该文构建了仅依赖哈希、异或及椭圆曲线模乘运算的轻量级认证流程,实现设备间的安全身份认证与会话密钥协商,更适用于资源受限终端。随后,该文通过形式化方法分析了方案安全性,证明其具备安全相互认证、会话密钥保密性与前向安全性,并能有效抵御重放与中间人等典型攻击。最后,通过实验对所提方案与现有先进方案进行了全面对比,结果验证了该文所提方案具备更低的计算和通信开销。Abstract:
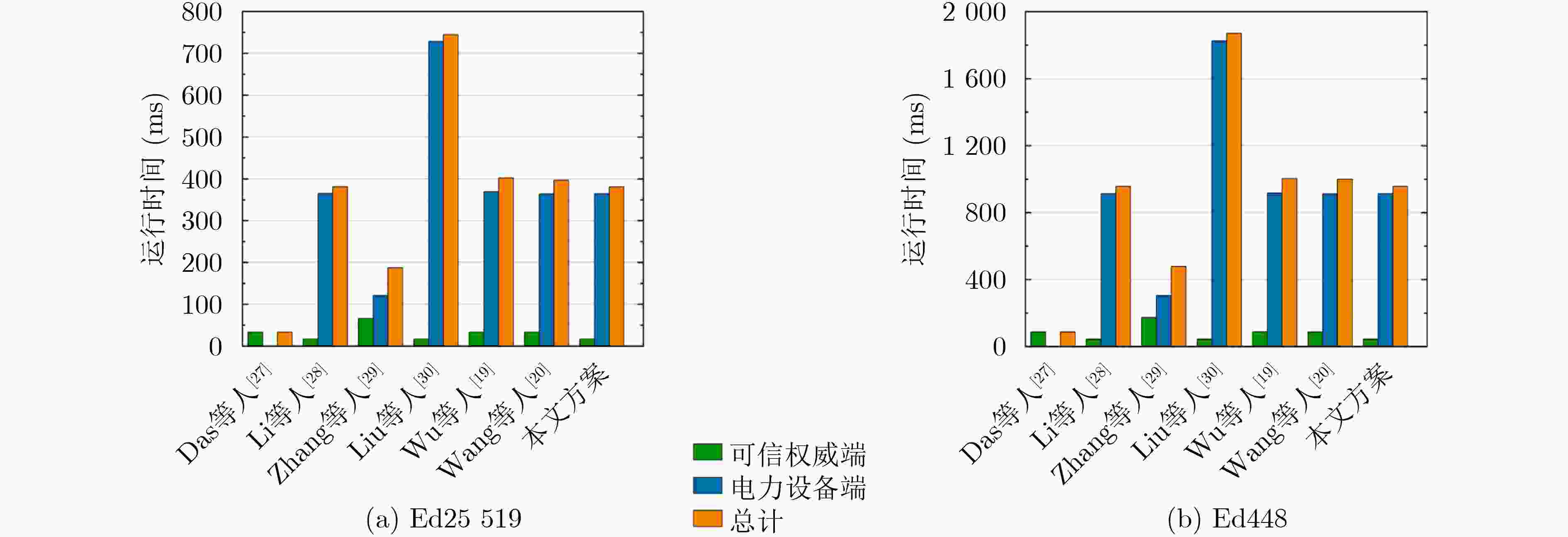
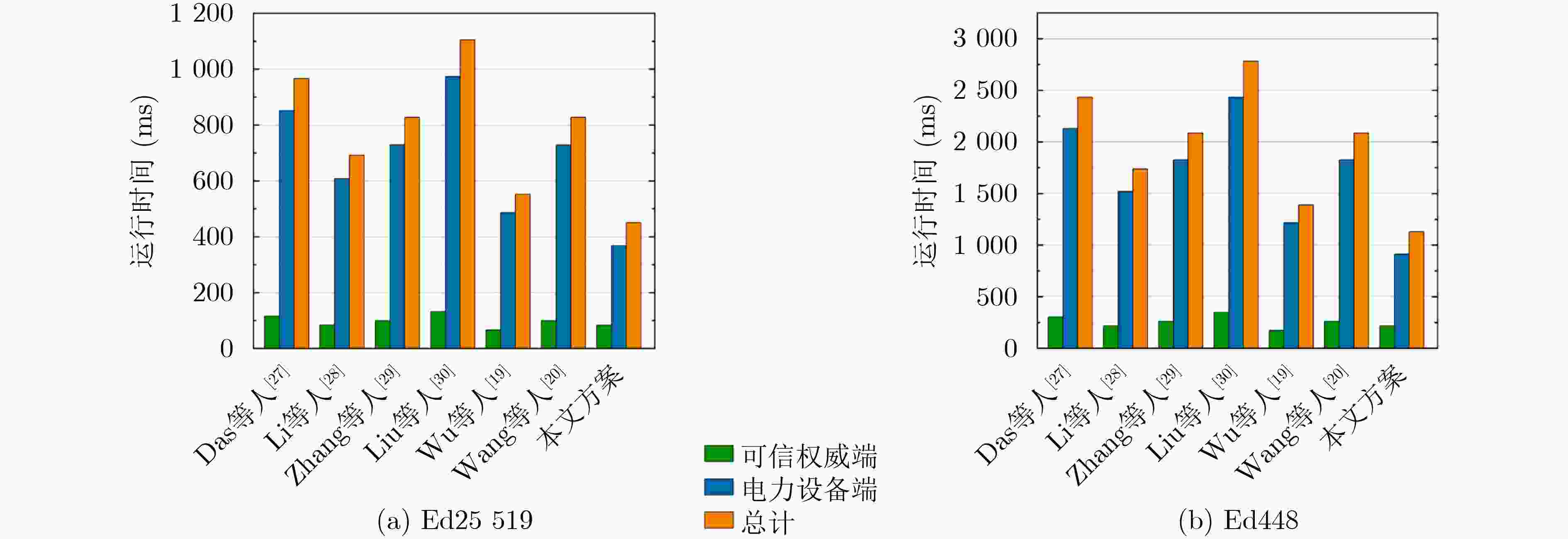
Objective The rapid development of the Internet of Things, cloud computing, and edge computing drives the evolution of the Power Industrial Internet of Things (PIIoT) into core infrastructure for smart power systems. In this architecture, terminal devices collect operational data and send it to edge gateways for preliminary processing before transmission to cloud platforms for further analysis and control. This structure improves efficiency, reliability, and security in power systems. However, the integration of traditional industrial systems with open networks introduces cybersecurity risks. Resource-constrained devices in PIIoT are exposed to threats that may lead to data leakage, privacy exposure, or disruption of power services. Existing authentication mechanisms either impose high computational and communication overhead or lack sufficient protection, such as forward secrecy or resistance to replay and man-in-the-middle attacks. This study focuses on designing a lightweight and secure authentication method suitable for the PIIoT environment. The method is intended to meet the operational needs of power terminal devices with limited computing capability while ensuring strong security protection. Methods A secure and lightweight identity authentication scheme is designed to address these challenges. Implicit certificate technology is applied during device identity registration, embedding public key authentication information into the signature rather than transmitting a complete certificate during communication. Compared with explicit certificates, implicit certificates are shorter and allow faster verification, reducing transmission and validation overhead. Based on this design, a lightweight authentication protocol is constructed using only hash functions, XOR operations, and elliptic curve point multiplication. This protocol supports secure mutual authentication and session key agreement while remaining suitable for resource-constrained power terminal devices. A formal analysis is then performed to evaluate security performance. The results show that the scheme achieves secure mutual authentication, protects session key confidentiality, ensures forward secrecy, and resists replay and man-in-the-middle attacks. Finally, experimental comparisons with advanced authentication protocols are conducted. The results indicate that the proposed scheme requires significantly lower computational and communication overhead, supporting its feasibility for practical deployment. Results and Discussions The proposed scheme is evaluated through simulation and numerical comparison with existing methods. The implementation is performed on a virtual machine configured with 8 GB RAM, an Intel i7-12700H processor, and Ubuntu 22.04, using the Miracl-Python cryptographic library. The security level is set to 128 bits, with the ed25519 elliptic curve, SHA-256 hash function, and AES-128 symmetric encryption. Table 1 summarizes the performance of the cryptographic primitives. As shown in Table 2 , the proposed scheme achieves the lowest computational cost, requiring three elliptic curve point multiplications on the device side and five on the gateway side. These values are substantially lower than those of traditional certificate-based authentication, which may require up to 14 and 12 operations, respectively. Compared with other representative authentication approaches, the proposed method further reduces the computational burden on devices, improving suitability for resource-limited environments.Table 3 shows that communication overhead is also minimized, with the smallest total message size (3 456 bits) and three communication rounds, attributed to the implicit certificate mechanism. As shown inFig. 5 , the authentication process exhibits the shortest execution time among all evaluated schemes. The runtime is 47.72 ms on devices and 82.88 ms on gateways, indicating lightweight performance and suitability for deployment in Industrial Internet of Things applications.Conclusions A lightweight and secure identity authentication scheme based on implicit certificates is presented for resource-constrained terminal devices in the PIIoT. Through the integration of a low-overhead authentication protocol and efficient certificate processing, the scheme maintains a balance between security and performance. It enables secure mutual authentication, protects session key confidentiality, and ensures forward secrecy while keeping computational and communication overhead minimal. Security analysis and experimental evaluation confirm that the scheme provides stronger protection and higher efficiency compared with existing approaches. It offers a practical and scalable solution for enhancing the security architecture of modern power systems. -
表 1 方案实现功能对比表
功能 [7] [9] [10] [11] [12] [13] [14] [15] [16] [17] [18] 本文方案 A1 √ × × √ √ √ √ √ √ √ √ √ A2 × √ √ √ √ × √ √ × × √ √ A3 × × × × × × √ × × × × √ A4 × × √ × √ √ × √ √ √ × √ A5 √ √ √ √ √ × √ × √ × × √ A6 × √ × √ √ √ × × × √ × √ A7 × × × × × √ × × × × × √ 注:A1–安全的相互认证;A2–共享密钥的安全生成;A3–前向保密性;A4–正式的安全性分析;A5–资源受限设备友好(计算效率);A6–资源受限设备友好(通信效率);A7–抵御内部攻击者;A8–认证类型(SCB–基于对称密码学的方案,PKCB–基于公钥密码学的方案)。 表 2 计算开销数值对比
方案 电力设备端 边缘网关端 总计 Das等人[24] $ 7\cdot {T}_{\rm{ecm}}+3\cdot {T}_{\rm{eca}}+6\cdot {T}_{\rm H} $ $ 7\cdot {T}_{\rm{ecm}}+3\cdot {T}_{\rm{eca}}+6\cdot {T}_{\rm H} $ $ 14\cdot {T}_{\rm{ecm}}+6\cdot {T}_{\rm{eca}}+12\cdot {T}_{\rm H} $ Li等人 [25] $ 5\cdot {T}_{\rm{ecm}}+2\cdot {T}_{\rm{eca}}+6\cdot {T}_{\rm H} $ $ 5\cdot {T}_{\rm{ecm}}+2\cdot {T}_{\rm{eca}}+6\cdot {T}_{\rm H} $ $ 10\cdot {T}_{\rm{ecm}}+4\cdot {T}_{\rm{eca}}+12\cdot {T}_{\rm H} $ Zhang等人 [26] $ 6\cdot {T}_{\rm{ecm}}+2\cdot {T}_{\rm{eca}}+2\cdot {T}_{\rm H} $ $ 6\cdot {T}_{\rm{ecm}}+2\cdot {T}_{\rm{eca}}+2\cdot {T}_{\rm H} $ $ 12\cdot {T}_{\rm{ecm}}+4\cdot {T}_{\rm{eca}}+4\cdot {T}_{\rm H} $ Liu等人 [27] $ 8\cdot {T}_{\rm{ecm}}+6\cdot {T}_{\rm{eca}} $ $ 8\cdot {T}_{\rm{ecm}}+6\cdot {T}_{\rm{eca}} $ $ 16\cdot {T}_{\rm{ecm}}+12\cdot {T}_{\rm{eca}} $ Wu等人 [17] $ 4\cdot {T}_{\rm{ecm}}+8\cdot {T}_{\rm H} $ $ 4\cdot {T}_{\rm{ecm}}+8\cdot {T}_{\rm H} $ $ 8\cdot {T}_{\rm{ecm}}+16\cdot {T}_{\rm H} $ Wang等人 [18] $ 6\cdot {T}_{\rm{ecm}}+{T}_{\rm{eca}}+3\cdot {T}_{\rm H} $ $ 6\cdot {T}_{\rm{ecm}}+{T}_{\rm{eca}}+3\cdot {T}_{\rm H} $ $ 12\cdot {T}_{\rm{ecm}}+2{T}_{\rm{eca}}+6\cdot {T}_{\rm H} $ 本文 $ 3\cdot {T}_{\rm{ecm}}+{T}_{\rm{eca}}+{T}_{{\mathrm{E}}}+5\cdot {T}_{\rm H} $ $ 5\cdot {T}_{\rm{ecm}}+2\cdot {T}_{\rm{eca}}+{T}_{{\mathrm{D}}}+5\cdot {T}_{\rm H} $ $ 8\cdot {T}_{\rm{ecm}}+3\cdot {T}_{\rm{eca}}+{T}_{{\mathrm{E}}}+{T}_{{\mathrm{D}}}+10\cdot {T}_{\rm H} $ 表 3 通信开销数值对比
方案 通信复杂度 通信总量 (bit) 交互轮次 Das等人[24] $ 6\cdot {L}_{\rm G}+6\cdot {L}_{\rm p}+2\cdot {L}_{\rm{ID}}+3\cdot {L}_{\rm T} $ 4928 3 Li等人 [25] $ 6\cdot {L}_{\rm G}+4\cdot {L}_{\rm p}+2\cdot {L}_{\rm{ID}} $ 4224 3 Zhang等人 [26] $ 8\cdot {L}_{\rm G}+3\cdot {L}_{\rm p}+3\cdot {L}_{\rm{ID}} $ 5056 6 Liu等人 [27] $ 8\cdot {L}_{\rm G}+4\cdot {L}_{\rm p}+4\cdot {L}_{\rm{ID}} $ 5376 6 Wu等人 [17] $ 2\cdot {L}_{\rm G}+4\cdot {L}_{\rm p}+3\cdot T $ 2240 3 Wang等人 [18] $ 6\cdot {L}_{\rm G}+4\cdot {L}_{\rm p} $ 4096 4 本文 $ 5\cdot {L}_{\rm G}+2\cdot {L}_{\rm p}+3\cdot {L}_{\rm{ID}}+3\cdot {L}_{{\mathrm{N}}} $ 3456 3 -
[1] LIU Mengxiang, TENG Fei, ZHANG Zhenyong, et al. Enhancing cyber-resiliency of DER-based smart grid: A survey[J]. IEEE Transactions on Smart Grid, 2024, 15(5): 4998–5030. doi: 10.1109/TSG.2024.3373008. [2] DEHGHANPOUR K, WANG Zhaoyu, WANG Jianhui, et al. A survey on state estimation techniques and challenges in smart distribution systems[J]. IEEE Transactions on Smart Grid, 2019, 10(2): 2312–2322. doi: 10.1109/TSG.2018.2870600. [3] SAHANI N, ZHU Ruoxi, CHO J H, et al. Machine learning-based intrusion detection for smart grid computing: A survey[J]. ACM Transactions on Cyber-Physical Systems, 2023, 7(2): 11. doi: 10.1145/3578366. [4] HU Chunqiang, LIU Zewei, LI Ruinian, et al. Smart contract assisted privacy-preserving data aggregation and management scheme for smart grid[J]. IEEE Transactions on Dependable and Secure Computing, 2024, 21(4): 2145–2161. doi: 10.1109/TDSC.2023.3300749. [5] PAGANINI P. Sodinokibi ransomware operators hit electrical energy company light S. A. [EB/OL]. https://securityaffairs.com/105477/cyber-crime/sodinokibi-ransomware-light-s-a.html, 2020. [6] DONG Jingnan, XU Guangxia, MA Chuang, et al. Blockchain-based certificate-free cross-domain authentication mechanism for industrial internet[J]. IEEE Internet of Things Journal, 2024, 11(2): 3316–3330. doi: 10.1109/JIOT.2023.3296506. [7] DAS A K, SHARMA P, CHATTERJEE S, et al. A dynamic password-based user authentication scheme for hierarchical wireless sensor networks[J]. Journal of Network and Computer Applications, 2012, 35(5): 1646–1656. doi: 10.1016/j.jnca.2012.03.011. [8] LEE J Y, LIN Weicheng, and HUANG Yuhung. A lightweight authentication protocol for internet of things[C]. The 2014 International Symposium on Next-Generation Electronics (ISNE), Kwei-Shan Tao-Yuan, China, 2014: 1–2. doi: 10.1109/ISNE.2014.6839375. [9] BRAEKEN A. Symmetric key based 5G AKA authentication protocol satisfying anonymity and unlinkability[J]. Computer Networks, 2020, 181: 107424. doi: 10.1016/j.comnet.2020.107424. [10] GHANI A, MANSOOR K, MEHMOOD S, et al. Security and key management in IoT‐based wireless sensor networks: An authentication protocol using symmetric key[J]. International Journal of Communication Systems, 2019, 32(16): e4139. doi: 10.1002/dac.4139. [11] BADAR H M S, QADRI S, SHAMSHAD S, et al. An identity based authentication protocol for smart grid environment using physical uncloneable function[J]. IEEE Transactions on Smart Grid, 2021, 12(5): 4426–4434. doi: 10.1109/TSG.2021.3072244. [12] ZHANG Yunru, HE Debiao, VIJAYAKUMAR P, et al. SAPFS: An efficient symmetric-key authentication key agreement scheme with perfect forward secrecy for industrial internet of things[J]. IEEE Internet of Things Journal, 2023, 10(11): 9716–9726. doi: 10.1109/JIOT.2023.3234178. [13] ABBASINEZHAD-MOOD D and NIKOOGHADAM M. Design and hardware implementation of a security-enhanced elliptic curve cryptography based lightweight authentication scheme for smart grid communications[J]. Future Generation Computer Systems, 2018, 84: 47–57. doi: 10.1016/j.future.2018.02.034. [14] GARG S, KAUR K, KADDOUM G, et al. Secure and lightweight authentication scheme for smart metering infrastructure in smart grid[J]. IEEE Transactions on Industrial Informatics, 2020, 16(5): 3548–3557. doi: 10.1109/TII.2019.2944880. [15] CHAUDHRY S A, NEBHAN J, YAHYA K, et al. A privacy enhanced authentication scheme for securing smart grid infrastructure[J]. IEEE Transactions on Industrial Informatics, 2022, 18(7): 5000–5006. doi: 10.1109/TII.2021.3119685. [16] HU Shunfang, CHEN Yanru, ZHENG Yilong, et al. Provably secure ECC-based authentication and key agreement scheme for advanced metering infrastructure in the smart grid[J]. IEEE Transactions on Industrial Informatics, 2023, 19(4): 5985–5994. doi: 10.1109/TII.2022.3191319. [17] WU Yapeng, GUO Hua, HAN Yiran, et al. A security-enhanced authentication and key agreement protocol in smart grid[J]. IEEE Transactions on Industrial Informatics, 2024, 20(9): 11449–11457. doi: 10.1109/TII.2024.3399915. [18] WANG Zhihao, HUO Ru, and WANG Shuo. A lightweight certificateless group key agreement method without pairing based on blockchain for smart grid[J]. Future Internet, 2022, 14(4): 119. doi: 10.3390/fi14040119. [19] SHAHIDINEJAD A, ABAWAJY J, and HUDA S. Highly-secure yet efficient blockchain-based CRL-free key management protocol for IoT-enabled smart grid environments[J]. IEEE Transactions on Information Forensics and Security, 2024, 19: 6738–6750. doi: 10.1109/TIFS.2024.3423724. [20] STINSON D R and STROBL R. Provably secure distributed schnorr signatures and a (t, n) threshold scheme for implicit certificates[C].The 6th Australasian Conference, ACISP 2001, Sydney, Australia, 2001: 417–434. doi: 10.1007/3-540-47719-5_33. [21] BRAEKEN A, CHIN Jijian, and TAN S Y. ECQV-IBI: Identity-based identification with implicit certification[J]. Journal of Information Security and Applications, 2021, 63: 103027. doi: 10.1016/j.jisa.2021.103027. [22] BLANCHET B. Modeling and verifying security protocols with the applied pi calculus and ProVerif[J]. Foundations and Trends® in Privacy and Security, 2016, 1(1/2): 1–135. doi: 10.1561/3300000004. [23] ZHENG Yue, LIU Wenye, GU Chongyan, et al. PUF-based mutual authentication and key exchange protocol for peer-to-peer IoT applications[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(4): 3299–3316. doi: 10.1109/TDSC.2022.3193570. [24] DAS A K, WAZID M, YANNAM A R, et al. Provably secure ECC-based device access control and key agreement protocol for IoT environment[J]. IEEE Access, 2019, 7: 55382–55397. doi: 10.1109/ACCESS.2019.2912998. [25] LI Sensen, ZHANG Tikui, YU Bin, et al. A provably secure and practical PUF-based end-to-end mutual authentication and key exchange protocol for IoT[J]. IEEE Sensors Journal, 2021, 21(4): 5487–5501. doi: 10.1109/JSEN.2020.3028872. [26] ZHANG Shiwen, YAN Ziwei, LIANG Wei, et al. BCAE: A blockchain-based cross domain authentication scheme for edge computing[J]. IEEE Internet of Things Journal, 2024, 11(13): 24035–24048. doi: 10.1109/JIOT.2024.3387934. [27] LIU Zewei, HU Chunqiang, RUAN Conghao, et al. An enhanced authentication and key agreement protocol for smart grid communication[J]. IEEE Internet of Things Journal, 2024, 11(12): 22413–22428. doi: 10.1109/JIOT.2024.3381379. -





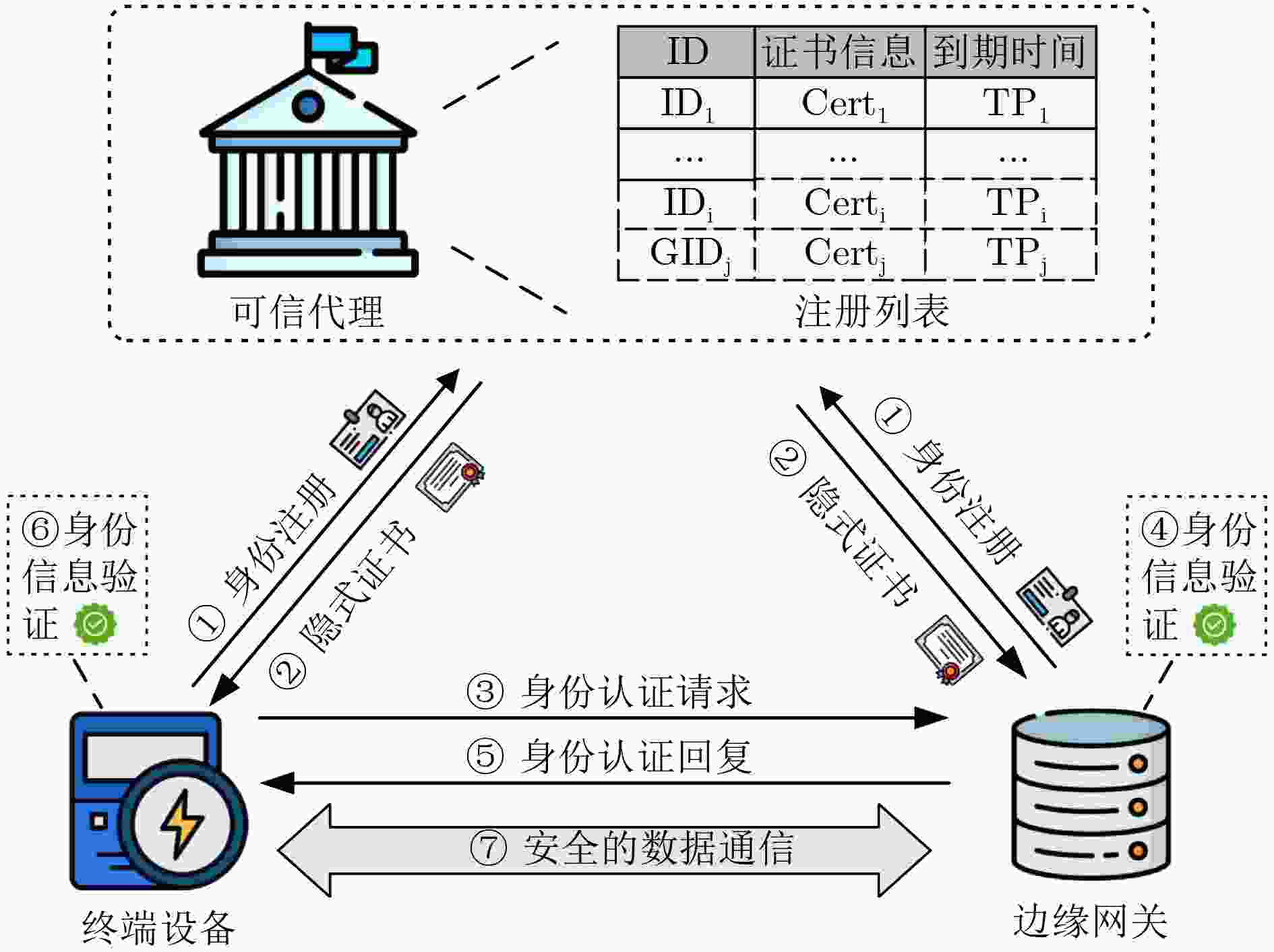
 下载:
下载:
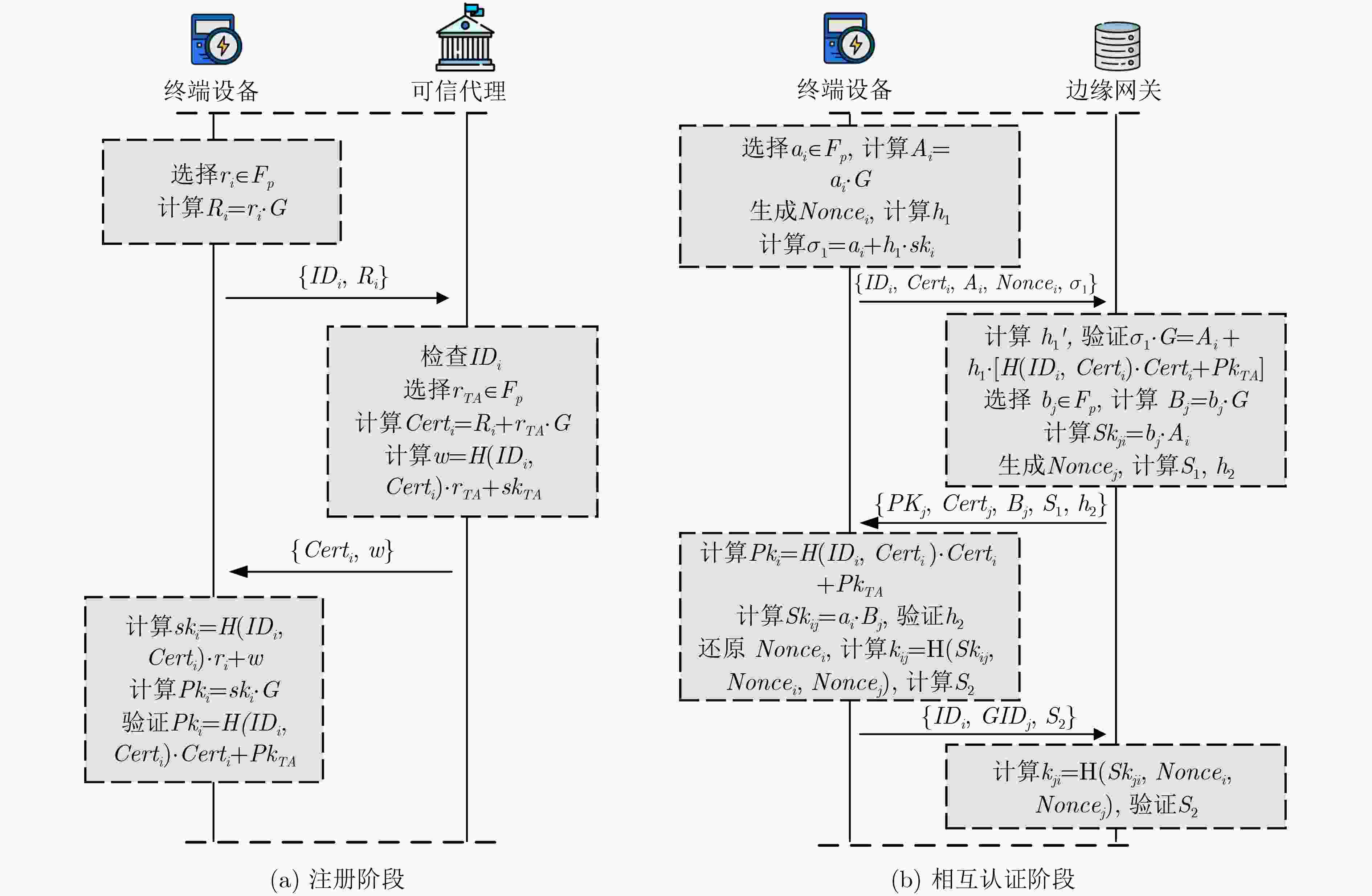
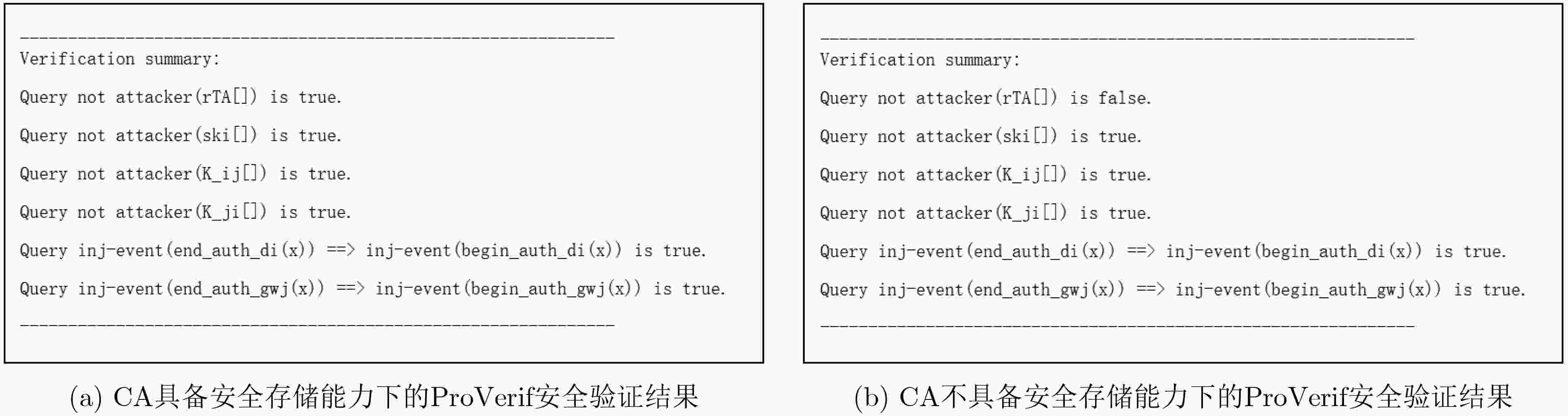


 下载:
下载:
