Unmanned Aircraft Vehicle-assisted Multi Cluster Concurrent Authentication Scheme for Internet of Things Devices
-
摘要: 为了应对物联网(IoT)设备在通过无人机(UAV)接入地面网络过程中可能面临的窃听和伪造攻击等安全威胁,以及避免因超海量设备并发接入导致的信令冲突和关键节点拥塞等问题,同时结合物联网设备低计算和存储能力等特点,利用物理不可克隆函数,该文提出一种基于无人机辅助的物联网设备多簇并发接入与切换认证方案。在该方案中,基于预共享密钥机制,无人机首先安全接入地面网络。随后,基于物理不可克隆函数,多簇物联网设备可以并发安全高效地通过无人机接入地面网,并且抵抗物理攻击、假冒攻击、中间人攻击等威胁,同时显著降低物联网设备侧的计算和存储开销。此外,当新无人机替换旧无人机时,多簇物联网设备可以并发安全高效地切换至新无人机,确保了设备网络服务的连续性。安全性和性能分析结果表明,该方案在计算和存储开销均较低的情况下,能够提供较为健壮的安全属性。此外,该方案在处理超海量设备并发接入时,能够有效减少信令开销,避免信令冲突和关键节点拥塞故障等问题。Abstract:
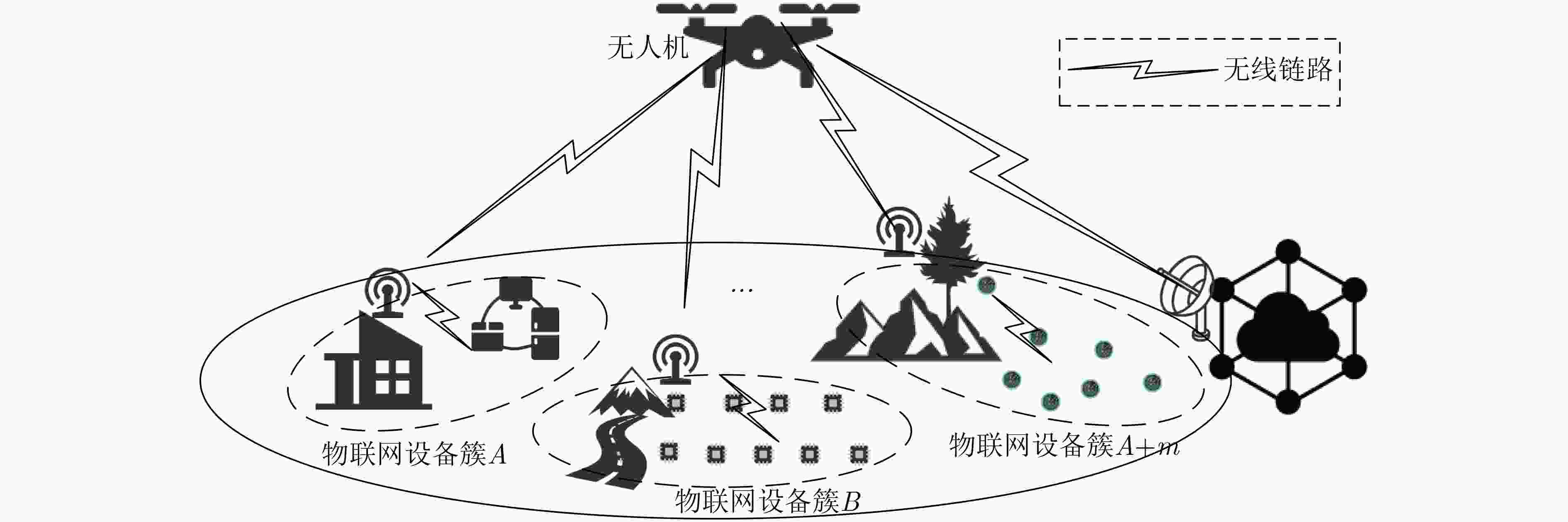
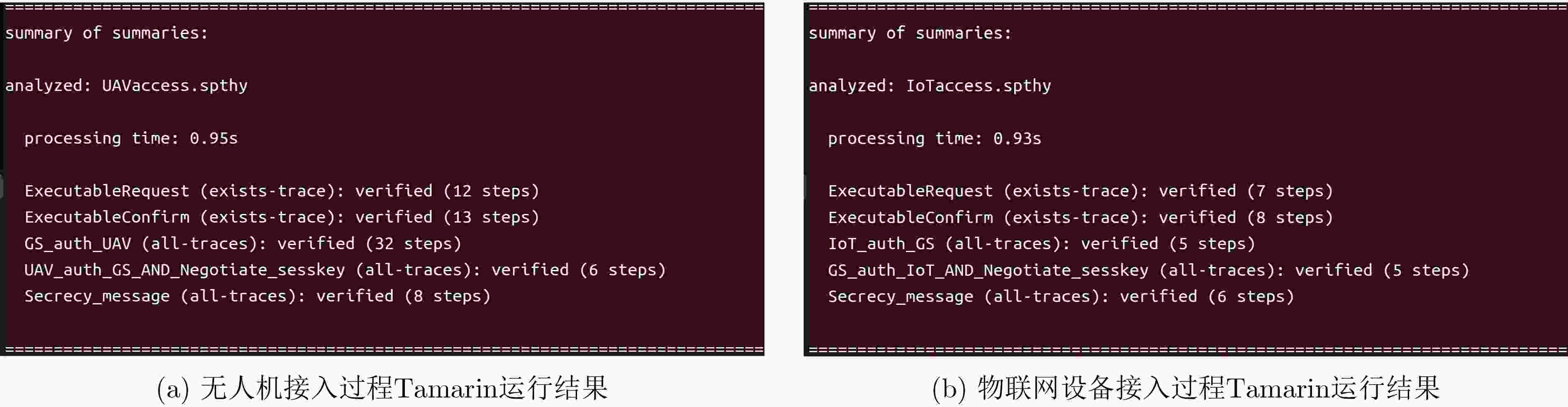
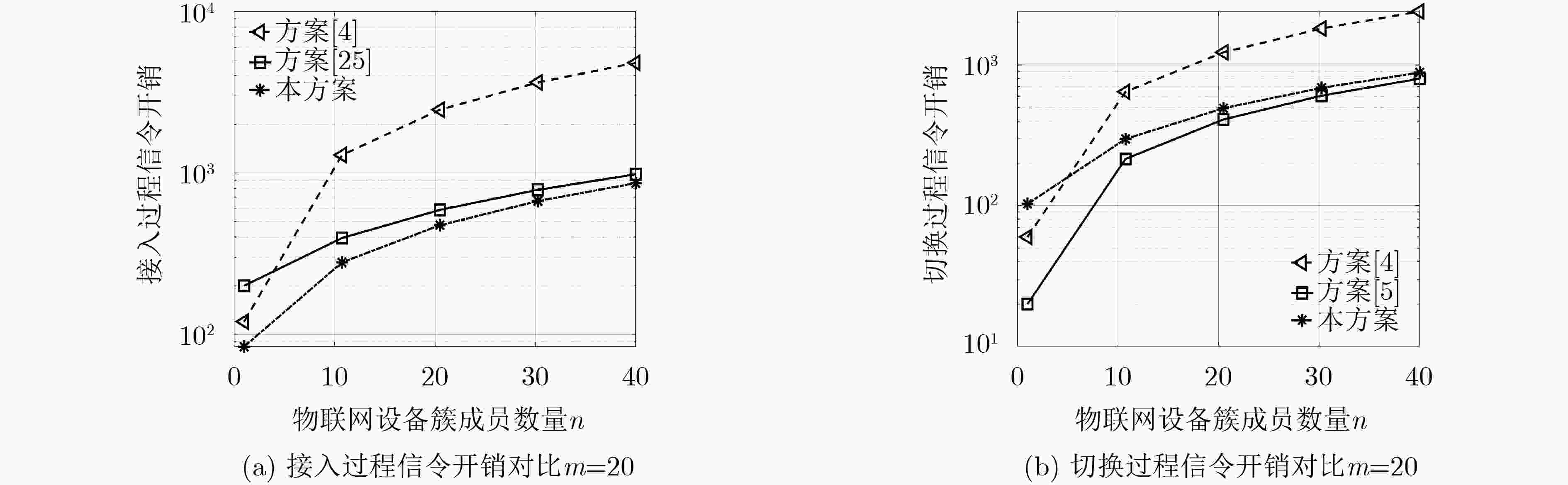
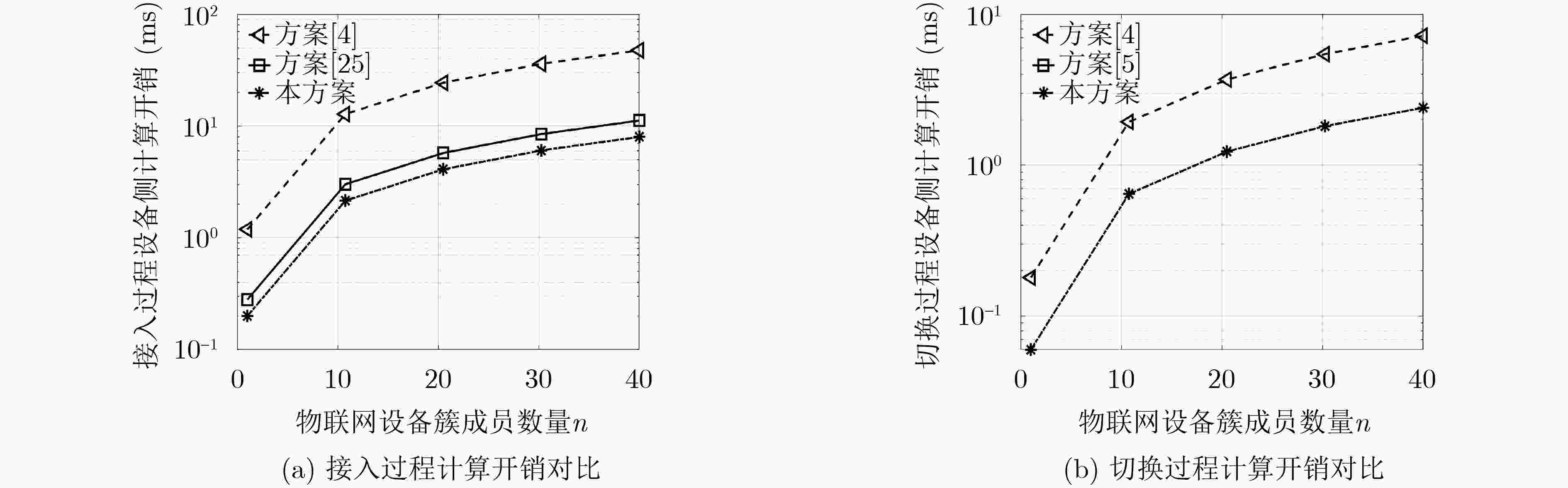
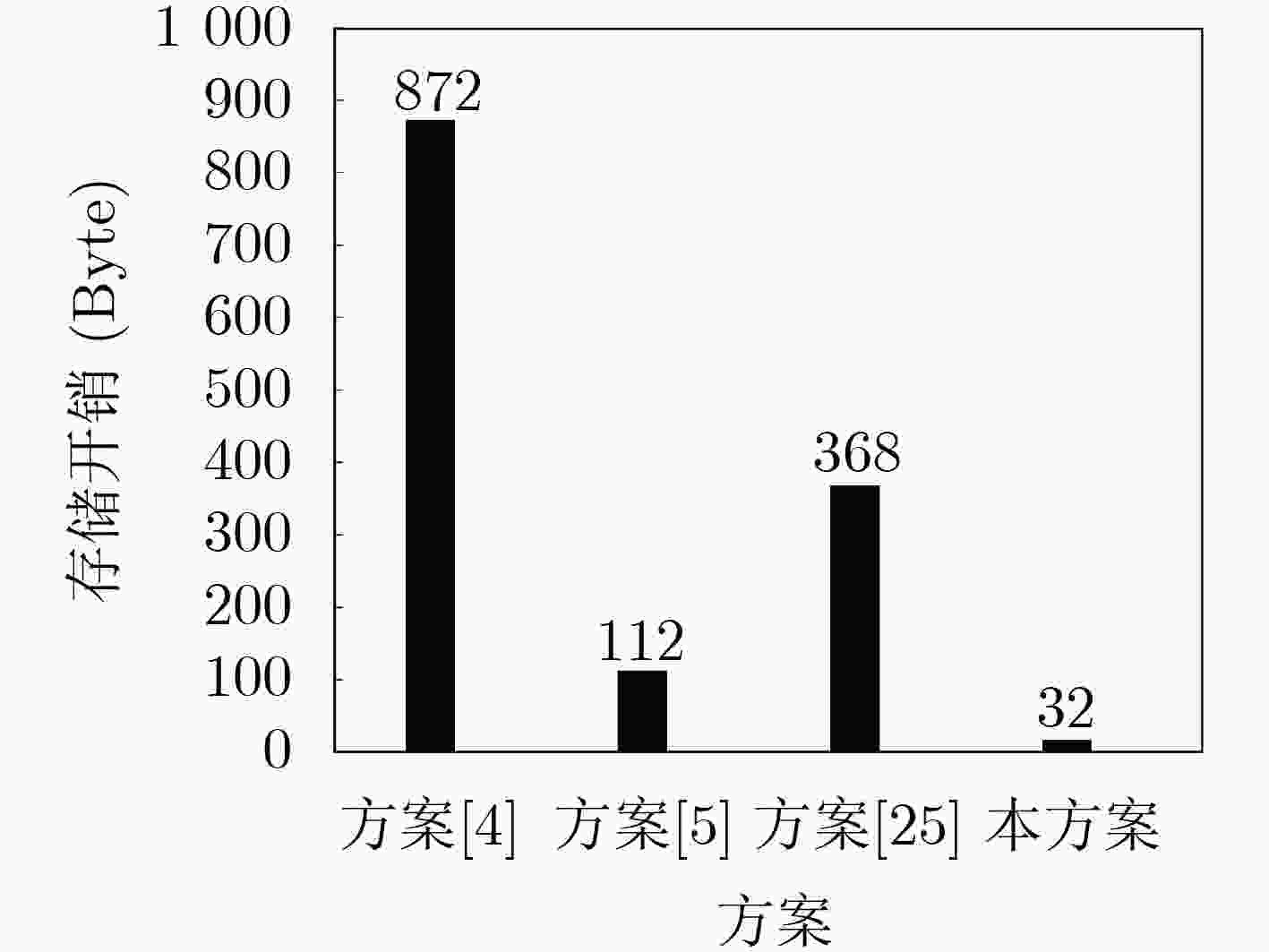
Objective With the rapid expansion of Internet of Things (IoT) devices, application scenarios such as smart cities and industrial intelligent manufacturing demand wider coverage and higher connection density from communication systems. Traditional terrestrial base stations have limited capacity to serve IoT devices in remote or complex environments. Unmanned Aircraft Vehicles (UAVs), owing to their flexible deployment and high mobility, can function as aerial base stations that effectively complement terrestrial networks, providing reliable and energy-efficient access for remote IoT terminals. Additionally, the expected 6G connectivity of tens of billions of devices may give rise to signaling conflicts and congestion at key nodes. To address these challenges, multi-cluster access schemes based on cluster division have been proposed. In these schemes, different clusters connect simultaneously to orthogonal subchannels, enabling UAVs to assist multiple IoT device clusters in accessing terrestrial networks concurrently. However, UAV-assisted multi-cluster communication faces pressing security and performance issues, including the susceptibility of air interface channels to attacks, the limited computational and storage capacities of IoT devices, signaling conflicts arising from massive concurrent access, and the requirement for seamless handover mechanisms due to the restricted endurance of UAVs. Therefore, the development of a secure and efficient UAV-assisted multi-cluster concurrent access and handover authentication scheme is essential. Methods This study proposes a secure authentication scheme for the UAV-assisted multi-cluster IoT device communication model, comprising four main components. First, UAV access authentication is achieved through a traditional pre-shared key mechanism, enabling mutual authentication and key agreement between the UAV and the ground network. Second, concurrent access authentication for multi-cluster IoT devices is realized using multi-layer aggregated signaling and aggregated message authentication code technologies, which effectively mitigate signaling conflicts and node congestion during massive concurrent access. Meanwhile, a Physically Unclonable Function (PUF) mechanism is incorporated to strengthen device-level security, protecting IoT devices against physical attacks while maintaining low storage and computational requirements. Finally, the UAV-assisted concurrent handover authentication integrates multi-layer aggregated signaling, aggregated message authentication code, and a pre-distribution key mechanism to enable fast and secure handovers between multi-cluster IoT devices and new UAVs, thereby ensuring the continuous security of network services. Results and Discussions The security of the proposed scheme is validated through formal analysis with the Tamarin tool, complemented by informal security analysis. The results show that the scheme satisfies mutual authentication and data security, and resists replay and man-in-the-middle attacks. The signaling overhead, as well as the computational and storage requirements of IoT devices during concurrent access and handover in multi-cluster communication, are also evaluated. The findings indicate that the scheme generates minimal signaling overhead ( Fig. 3 ), thereby preventing signaling conflicts and node congestion. Moreover, the computational cost on devices remains low (Fig. 4 ), and the storage demand is minimal (Fig. 5 ), demonstrating that the scheme is well suited for resource-constrained IoT devices.Conclusions This paper proposes a UAV-assisted authentication scheme for concurrent access and handover of multi-cluster IoT devices. In this scheme, UAVs can securely and efficiently access the ground network, while multi-cluster IoT devices achieve concurrent and secure access through UAVs and perform rapid authentication and key agreement during handover to a new UAV. Security and performance analyses demonstrate that the scheme ensures multiple security properties, including mutual authentication, data security, and resistance to replay, man-in-the-middle, and physical attacks, while maintaining low computational and storage overhead on IoT devices. In addition, the scheme features low signaling overhead, effectively preventing signaling conflicts and key node congestion during large-scale concurrent access. Nevertheless, some limitations remain. Future work will explore more comprehensive and practical authentication mechanisms. Specifically, lightweight dynamic key update mechanisms tailored to UAV communication scenarios will be investigated to enhance security with minimal overhead. To address design complexity and environmental adaptability issues caused by PUF hardware dependence, more robust hardware security mechanisms will be considered to improve system stability in complex environments. Moreover, to mitigate the computational and energy burden on UAVs resulting from aggregation and forwarding tasks, approaches such as edge computing offloading will be examined to enable dynamic task allocation and load balancing, ensuring efficient and sustainable operation. Finally, a prototype system will be developed, and field experiments will be conducted to validate the feasibility and performance of the proposed solution in real-world scenarios. -
表 1 信令开销(m个簇,n个簇成员)
表 2 关键节点单个时间内接收到的最大信令数
表 3 物联网设备侧主要密码学计算操作
-
[1] MACH P and BECVAR Z. Mobile edge computing: A survey on architecture and computation offloading[J]. IEEE Communications Surveys & Tutorials, 2017, 19(3): 1628–1656. doi: 10.1109/COMST.2017.2682318. [2] ZHANG Zhanpeng, XU Chen, LI Zewu, et al. Deep reinforcement learning for aerial data collection in hybrid-powered NOMA-IoT networks[J]. IEEE Internet of Things Journal, 2023, 10(2): 1761–1774. doi: 10.1109/JIOT.2022.3209980. [3] 3GPP. Study on security aspects of uncrewed aerial systems (UAS) (Release 17)[R]. 3GPP TR 33.854 V0.4. 0, 2021. [4] MA Ruhui, CAO Jin, HE Shiyang, et al. A UAV-assisted UE access authentication scheme for 5G/6G network[J]. IEEE Transactions on Network and Service Management, 2024, 21(2): 2426–2444. doi: 10.1109/TNSM.2023.3341829. [5] AYDIN Y, KURT G K, OZDEMIR E, et al. Group handover for drone base stations[J]. IEEE Internet of Things Journal, 2021, 8(18): 13876–13887. doi: 10.1109/JIOT.2021.3068297. [6] CHOI J, KWON D, SON S, et al. A PUF-based lightweight authentication scheme for UAV-assisted internet of vehicles[J]. IEEE Transactions on Intelligent Transportation Systems, 2025. doi: 10.1109/TITS.2025.3564581. [7] NIKOOGHADAM M, AMINTOOSI H, ISLAM S K H, et al. A provably secure and lightweight authentication scheme for internet of drones for smart city surveillance[J]. Journal of Systems Architecture, 2021, 115: 101955. doi: 10.1016/j.sysarc.2020.101955. [8] BERINI A D E, FERRAG M A, FAROU B, et al. HCALA: Hyperelliptic curve-based anonymous lightweight authentication scheme for internet of drones[J]. Pervasive and Mobile Computing, 2023, 92: 101798. doi: 10.1016/j.pmcj.2023.101798. [9] YU S, DAS A K, and PARK Y. RLBA-UAV: A robust and lightweight blockchain-based authentication and key agreement scheme for PUF-enabled UAVs[J]. IEEE Transactions on Intelligent Transportation Systems, 2024, 25(12): 21697–21708. doi: 10.1109/TITS.2024.3480029. [10] BANSAL G and SIKDAR B. A secure and efficient mutual authentication protocol framework for unmanned aerial vehicles[C]. The 2021 IEEE Globecom Workshops (GC Wkshps), Madrid, Spain, 2021: 1–6. doi: 10.1109/GCWkshps52748.2021.9682006. [11] ALLADI T, VENKATESH V, CHAMOLA V, et al. Drone-MAP: A novel authentication scheme for drone-assisted 5G networks[C]. The IEEE INFOCOM 2021 - IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Vancouver, Canada, 2021: 1–6. doi: 10.1109/INFOCOMWKSHPS51825.2021.9484594. [12] BANSAL G and SIKDAR B. Achieving secure and reliable UAV authentication: A Shamir’s secret sharing based approach[J]. IEEE Transactions on Network Science and Engineering, 2024, 11(4): 3598–3610. doi: 10.1109/TNSE.2024.3381599. [13] PU Cong, WALL A, CHOO K K R, et al. A lightweight and privacy-preserving mutual authentication and key agreement protocol for internet of drones environment[J]. IEEE Internet of Things Journal, 2022, 9(12): 9918–9933. doi: 10.1109/JIOT.2022.3163367. [14] KHAN M A, ULLAH I, ALKHALIFAH A, et al. A provable and privacy-preserving authentication scheme for UAV-enabled intelligent transportation systems[J]. IEEE Transactions on Industrial Informatics, 2022, 18(5): 3416–3425. doi: 10.1109/TII.2021.3101651. [15] LOUNIS K, DING S H H, and ZULKERNINE M. D2D-MAP: A drone to drone authentication protocol using physical unclonable functions[J]. IEEE Transactions on Vehicular Technology, 2023, 72(4): 5079–5093. doi: 10.1109/TVT.2022.3224611. [16] ALLADI T, NAREN, BANSAL G, et al. SecAuthUAV: A novel authentication scheme for UAV-ground station and UAV-UAV communication[J]. IEEE Transactions on Vehicular Technology, 2020, 69(12): 15068–15077. doi: 10.1109/TVT.2020.3033060. [17] KARMAKAR R, KADDOUM G, and AKHRIF O. A PUF and fuzzy extractor-based UAV-ground station and UAV-UAV authentication mechanism with intelligent adaptation of secure sessions[J]. IEEE Transactions on Mobile Computing, 2024, 23(5): 3858–3875. doi: 10.1109/TMC.2023.3284216. [18] LIU Chunpeng, HUANG Tao, and MA Maode. UAP: A system authentication protocol for UAV relay communication by UAV-assisted[J]. IEEE Open Journal of Vehicular Technology, 2025, 6: 1539–1550. doi: 10.1109/OJVT.2025.3567079. [19] LI Jinguo, WEN Mi, and ZHANG Tao. Group-based authentication and key agreement with dynamic policy updating for MTC in LTE-A networks[J]. IEEE Internet of Things Journal, 2016, 3(3): 408–417. doi: 10.1109/JIOT.2015.2495321. [20] CAO Jin, YAN Zheng, MA Ruhui, et al. LSAA: A lightweight and secure access authentication scheme for both UE and mMTC devices in 5G networks[J]. IEEE Internet of Things Journal, 2020, 7(6): 5329–5344. doi: 10.1109/JIOT.2020.2976740. [21] CAO Jin, YU Pu, MA Maode, et al. Fast authentication and data transfer scheme for massive NB-IoT devices in 3GPP 5G network[J]. IEEE Internet of Things Journal, 2019, 6(2): 1561–1575. doi: 10.1109/JIOT.2018.2846803. [22] CAO Jin, YU Pu, XIANG Xinyin, et al. Anti-quantum fast authentication and data transmission scheme for massive devices in 5G NB-IoT system[J]. IEEE Internet of Things Journal, 2019, 6(6): 9794–9805. doi: 10.1109/JIOT.2019.2931724. [23] NAKKAR M, ALTAWY R, and YOUSSEF A. GASE: A lightweight group authentication scheme with key agreement for edge computing applications[J]. IEEE Internet of Things Journal, 2023, 10(1): 840–854. doi: 10.1109/JIOT.2022.3204335. [24] ZHANG Xiaoyi, WU Huici, TAO Xiaofeng, et al. PUF-based lightweight group authentication for massive IoT access with insecure channel[J]. IEEE Internet of Things Journal, 2025, 12(14): 26968–26983. doi: 10.1109/JIOT.2025.3561943. [25] REN Xiongpeng, CAO Jin, MA Maode, et al. A novel PUF-based group authentication and data transmission scheme for NB-IoT in 3GPP 5G networks[J]. IEEE Internet of Things Journal, 2022, 9(5): 3642–3656. doi: 10.1109/JIOT.2021.3098224. [26] RAJ K, BODAPATI S, and CHATTOPADHYAY A. PUF-based lightweight mutual authentication protocol for internet of things (IoT) devices[C]. The 2024 IEEE International Symposium on Circuits and Systems (ISCAS), Singapore, Singapore, 2024: 1–5. doi: 10.1109/ISCAS58744.2024.10558672. [27] DOLEV D and YAO A C. On the security of public key protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198–208. doi: 10.1109/TIT.1983.1056650. [28] CAO Jin, LI Sheng, MA Ruhui, et al. RPRIA: Reputation and PUF-based remote identity attestation protocol for massive IoT devices[J]. IEEE Internet of Things Journal, 2022, 9(19): 19174–19187. doi: 10.1109/JIOT.2022.3164174. [29] 3GPP. 3GPP TS 38.300-2025 NR; NR and NG-RAN overall description; Stage-2 (Release 15)[S]. Valbonne: 3GPP, 2025. [30] MEIER S, SCHMIDT B, CREMERS C, et al. The TAMARIN prover for the symbolic analysis of security protocols[C]. The 25th International Conference on Computer Aided Verification, Saint Petersburg, Russia, 2013: 696–701. doi: 10.1007/978-3-642-39799-8_48. [31] BASIN D, CREMERS C, KIM T H J, et al. Design, analysis, and implementation of ARPKI: An attack-resilient public-key infrastructure[J]. IEEE Transactions on Dependable and Secure Computing, 2018, 15(3): 393–408. doi: 10.1109/TDSC.2016.2601610. [32] BASIN D, DREIER J, HIRSCHI L, et al. A formal analysis of 5G authentication[C]. The 2018 ACM SIGSAC Conference on Computer and Communications Security, Toronto, Canada, 2018: 1383–1396. doi: 10.1145/3243734.3243846. [33] REN Xiongpeng, CAO Jin, NIU Ben, et al. A formal analysis of 5G ProSe AKA protocols for U2N relay communication[J]. IEEE Transactions on Dependable and Secure Computing, 2025, 22(3): 2909–2924. doi: 10.1109/TDSC.2024.3522895. [34] National Institute of Standards and Technology. Recommendation for key management: Part 1–General[R]. NIST SP 800-57 PART 1 REV. 5, 2020. -





 下载:
下载:


 下载:
下载:
